Non-disruptive deployment, Enclave works alongside existing solutions. Install on one, or one thousand devices without rip and replace, and roll out easily via RMM without additional hardware or proxies to deploy.
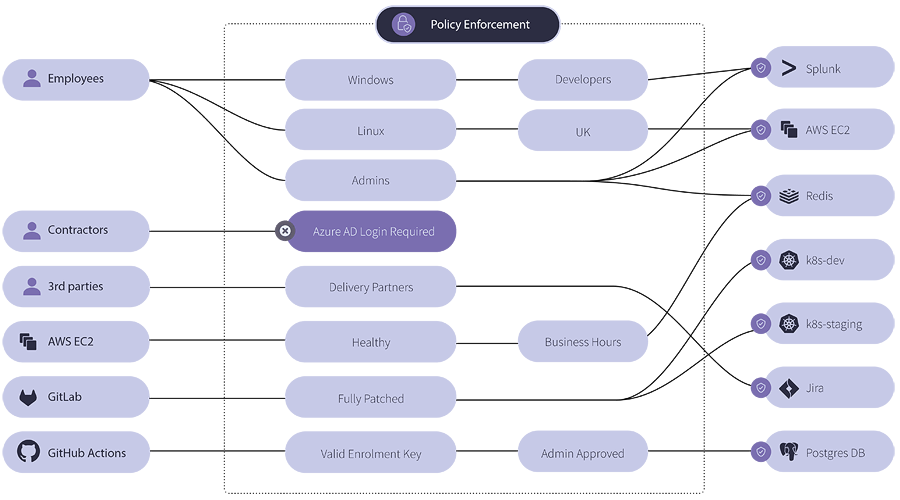
Enclave’s intuitive visual policy engine is delivered in a non-technical, cloud-based management platform which makes it simple to arrange private access, and easy to reason about the state of the network.
Built for channel; Our Partner Portal allows MSPs and Systems Integrators to manage multiple customer accounts, apply industry discounts and integrate billing with PSA tooling.
Unleash the Power of Precision Access. Building one-to-one connections, Enclave cloaks your applications with invisible network access gates which only materialise when certain trust standards are met to protect against discovery, targeting and attack.
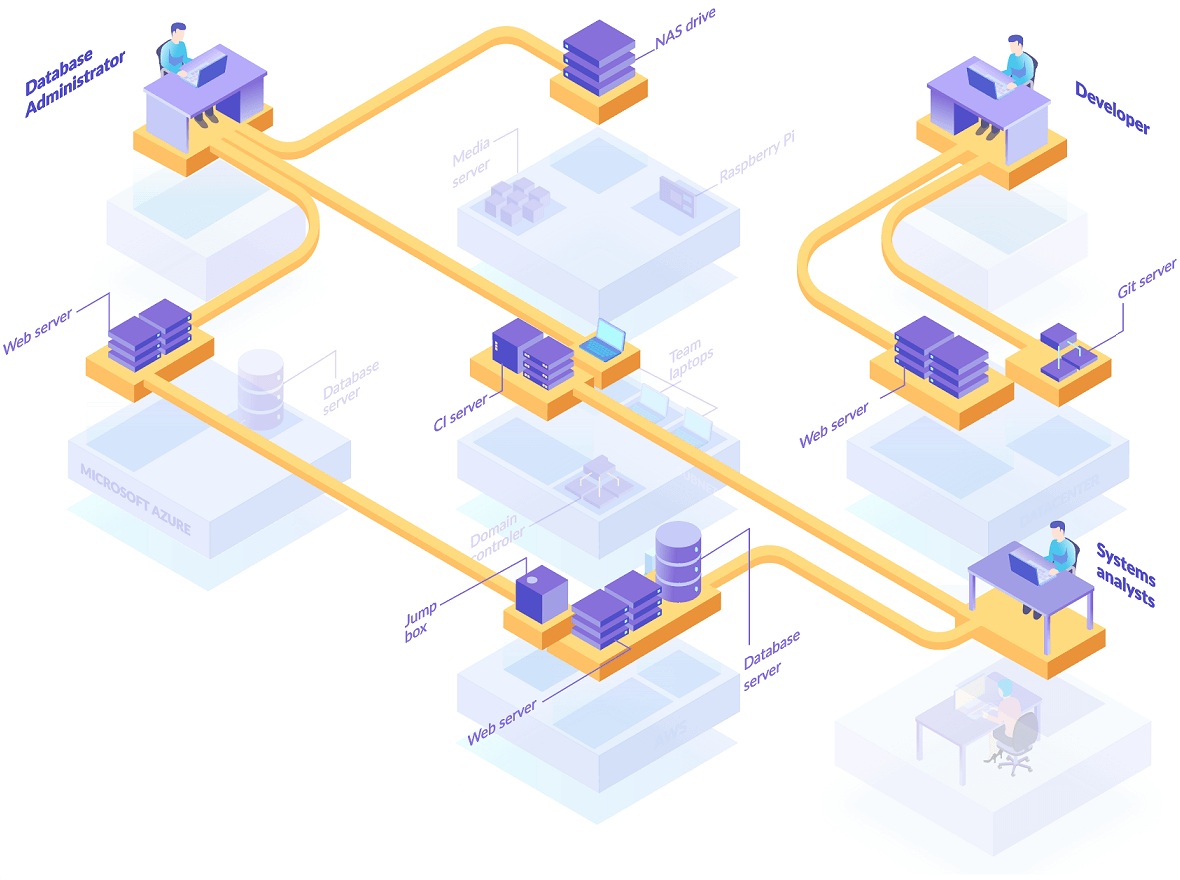
Enclave can help to transform your security landscape, enabling you to safely connect specific staff, contractors, partners, supply chains and production systems together without needing to think about firewalls, subnets, VPNs or ACLs.
“The rise of remote workers has made it a lot harder for our clients to secure their perimeter with the traditional approach of using VPNs and firewalls. Enclave’s easy to deploy and use solution makes the journey to zero trust a whole lot easier for our clients. We look forward to a fruitful partnership.”
“Enclave helped eliminate single points of failure in the network for WJEC, offering an alternative to complex, difficult to maintain hardware-based VPN servers. It’s a really powerful solution that’s more cost-effective for us than other alternatives, and works across all of our Cloud providers, physical locations and technologies.”
“We prefer Enclave over Traditional VPN, it’s a higher performance, more secure option to get remote access to your data and applications independent of where those applications or data resides. It allows us to increase our client’s security posture through an easy to understand end user interface.”
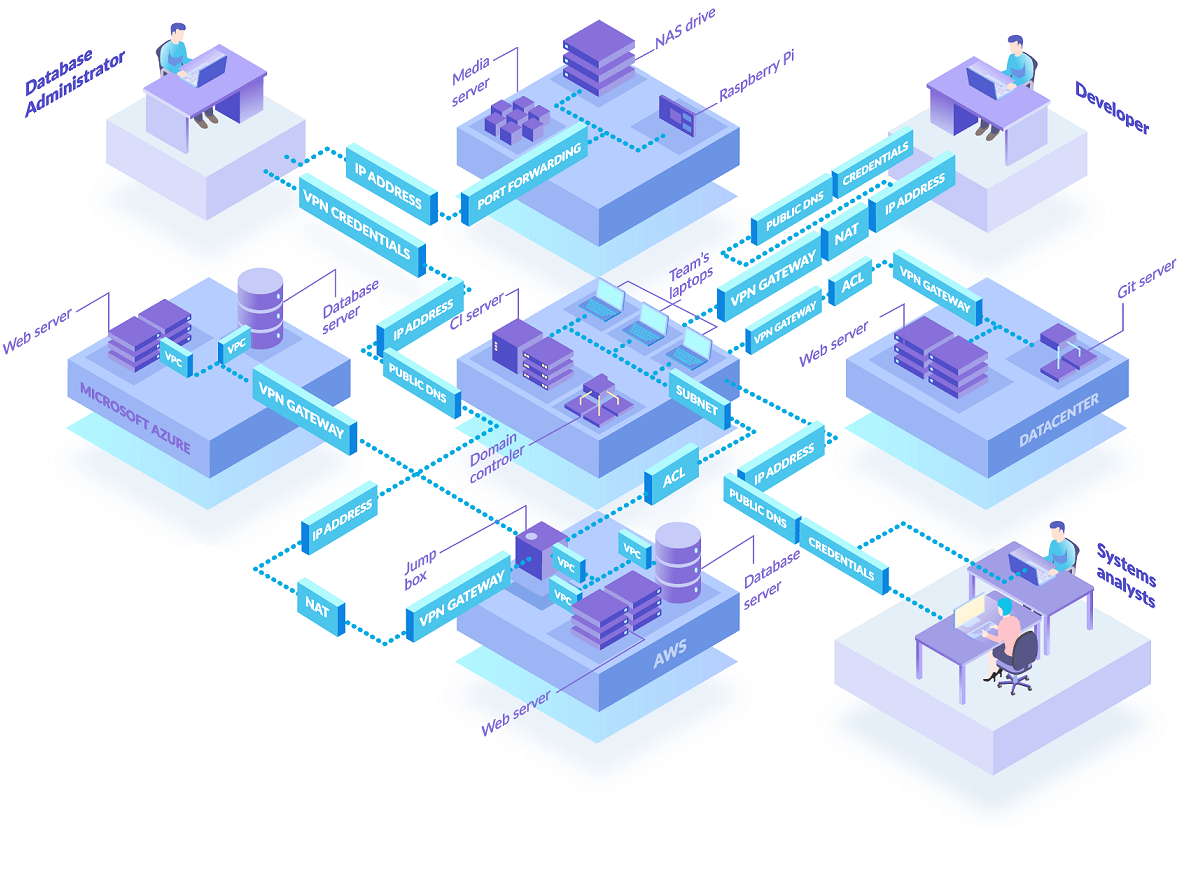
With open ports exposed to the public Internet, VPN servers are a magnet for attackers, risking information disclosure, credential stuffing, and targeted zero-day exploits. VPNs are also slow to setup and hard to change with lots of moving parts. They inefficiently force traffic through central locations and place users directly onto the local network, which can expose the whole company and their partners to attack.
Unlike traditional VPN servers, Enclave cuts out the middle-man by directly connecting workloads and devices together for the most efficient use of networks and bandwidth to deliver a better user experience.
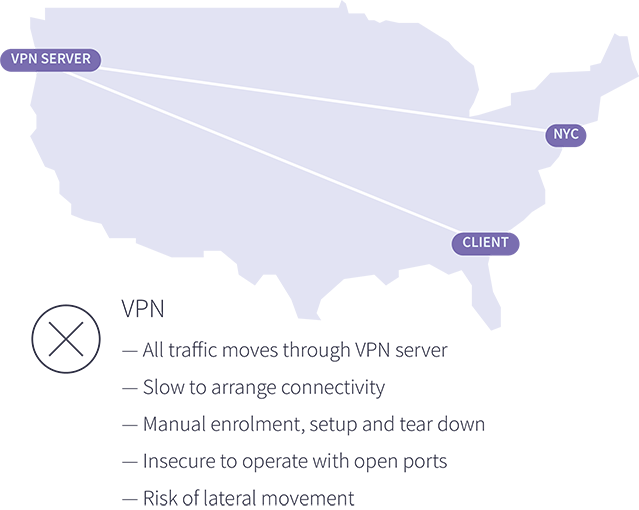
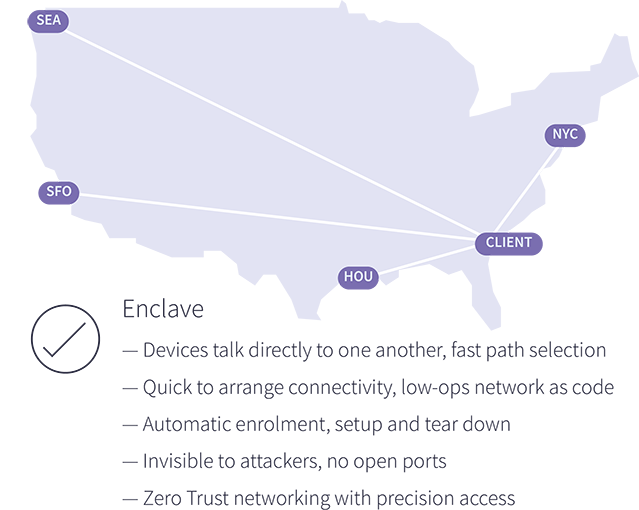
Deploying Enclave and Zero Trust Network Access to replace traditional VPN servers can help your customers succeed in a variety of scenarios.
Our easy to deploy solution makes it simple to replace old VPN servers incrementally, one system at a time if necessary, to quickly upgrade your customers to modern private access without needing to rip out their existing infrastructure first.
By deploying Enclave, organisations can improve the speed and efficiency of private access while removing the need to directly expose workloads and applications to the Internet. Integrating Enclave with IdP vendors such as Azure allows organisations to take advantage of technologies like Conditional Access and Privileged access manager (PIM) to enforce a single, consistent set of access controls across the business, making Enclave a great way to replace legacy VPN servers with modern, Zero Trust Network Access (ZTNA) solution.
Enclave can be used as a trusted pathway to common SaaS services and cloud platforms like Office 365, Azure, AWS, Google and Salesforce with IP-based whitelist access. By routing all traffic for a selected SaaS service via specific Enclave system on a static IP address, SaaS platforms can be configured to restrict access to customer accounts by whitelisting access from only the known static IP address.
Enclave makes it easy to connect systems separated by firewalls, VMs, containers and NAT, even if they’re both on dynamic IP addresses. Using only outbound traffic and a simple policy editor to define the desired connectivity, Enclave removes the hassle of configuring firewalls and VPNs, or needing to manage DNS, IP addresses, subnets, ACLs, NAT, routing tables, certificates and secret keys.

By default, Enclave is an overlay network: it only routes traffic between devices running Enclave. But administrators can set Enclave to route some, or all Internet traffic through one (or more) Enclave systems. This means that when a system running Enclave with a static public IP is routing traffic for other member systems, other parties can use Enclave to share that same static IP address to reach the Internet.

Enclave makes it easy to add multi-factor authentication to services like Remote Desktop, or to add time constraints and conditional access policies integrated with Azure Active Directory to tightly control access for systems architects, system administrators and SREs to gain private access to management interfaces.
Use Enclave to authorise time-limited access, audit connections and require MFA to access systems which don’t natively support multi-factor authentication like RDP and Windows file shares.
Enclave is designed to be installed directly onto every client, server, cloud instance, virtual machine and container in your organisation. That way, Enclave can apply Zero Trust Network Access principles and controls between systems, fully enforce policy and provide end-to-end encryption. However, in some situations, you can’t or might not want to install Enclave on all devices or systems. In these cases, you can set up an Enclave Gateway to provide access to such devices and systems like RDS databases, webcams, printers and IoT / OT sensors and devices or adjacent subnets.
Engineers are at the forefront of innovation, constantly pushing boundaries to drive technological advancements. At Enclave, we understand the unique challenges engineering teams face when it comes to protecting intellectual property, securing sensitive data, and maintaining productivity.

Grant developers and DevOps practitioners anywhere, anytime private access to a broad range of technologies and platforms like Kubernetes and enable Lambda functions and GitHub Actions to access on-prem resources. Use Enclave to protect access to development environments, Kubernetes clusters, as well as on-premise and cloud environments and break-glass access to staging and production environments. Use special ephemeral enrolment keys to un-enroll containers automatically once terminated.

Effortlessly build cloud-agnostic private network connectivity. An Enclave network backplane connects resources, workloads and users across datacenters, multi-cloud and hybrid environments with a single, consistent set of security controls that give only the necessary access, and no more.
Enclave Gateway allows you to protect access to everything; be it access to legacy on-prem services, or even the entire Internet.
Deploy an Enclave Gateway yourself to integrate with any existing network protections, or use our Managed Gateway service to route all your user’s internet traffic through hardware we manage for you, with built-in DNS filtering to bolster protection against malware and other online threats. All without having to worry about managing the device yourself.
Enclave works everywhere you do, and with extensive APIs some customers use Enclave to build ChatOps workflows linking tools like Slack and Microsoft Teams with Enclave APIs to enable self-service private access to internal workloads.

Supported Operating Systems & Platforms