
DevOps and ZTNA
The Ultimate Agility Enabler
DevOps is the leading concept for companies looking to accelerate and simplify the development and deployment of new software. Combining Development and Operations into one smooth process has many advantages, as the teams work together in a continuous iterative process. The DevOps model may be Agile, but gaining private access to the working environments very often is not.
Remote access and DevOps
When so many teams are working remotely from various locations, ensuring secure, reliable remote access is a challenge for many organizations. Here are just some of the issues:
-
Access Management is incredibly complex – not only the onboarding of new users but also of tools and services. Setting up this up can cause significant delays.
-
Teams often rotate through time zones – consisting of internal employees that follow the sun, contractors, and other third parties, for which access must be provided, changed, and removed at different times.
-
BYOD adds additional complexity – as contractors and third parties often use their own devices, and additional tools, which can present an additional security risk.
-
Least privilege access – to multiple systems and services individually via separate secured sessions can be time-consuming and complicated and require different approaches in different places.
-
Expecting developers to come down to the ops tooling – means valuable resources are consumed with the monitoring of security policies and access rights and implementation details of the network.
-
Hybrid infrastructure – on-premise, cloud, multi-cloud and multi-region only adds additional layers of complexity.
The result is a whole lot of frustration and delays as system administrators battle to get the teams and the infrastructure working seamlessly together. And that’s not to mention the additional, and potentially even more serious, security challenge of protecting the development process from external threats. Not just a pain during the project phase, a security breach at this level could leave the source code vulnerable to threat actors, and potentially even destroy the business.
How can companies protect their most valuable assets without slowing the project? The traditional security options, such as VPNs, are cumbersome and susceptible to attack. We need something that will get out of the way of the work while providing superior protection.
DevOps and Zero Trust Network Access
The answer is Zero Trust Network Access – or ZTNA. As the name suggests, ‘Zero Trust’ means that no person or tool (human user or technical application) should be automatically trusted, and access must be constantly verified once it is provided. Zero trust is a concept, not a tool or a service, and ZTNA is an enabling technology that provides secure access to workloads and resources based on the zero-trust principles.
Going back to our list of challenges, what advantages does ZTNA have for DevOps remote access?
With ZTNA, access management is simplified. Remote access for all DevOps users and services is managed with a unified service manager. Security teams have more control with a (mostly) unified and streamlined setup, allowing for a high degree of automation. Access is provided to users depending on their role, with a least-privilege approach.
Onboarding for new users is completed in a single session, rather than having to set up VPNs access, modify firewalls, authenticate sessions or any of the other time-consuming tasks that traditionally would be needed. Adding, changing, or removing access to a user or user group takes minutes, not hours – or even days. The simplicity of ZTNA reduces the risk of mistakes and the unexpected consequences of ‘yak shaving’, where a simple change kicks off a chain reaction of unplanned but necessary changes and tasks.
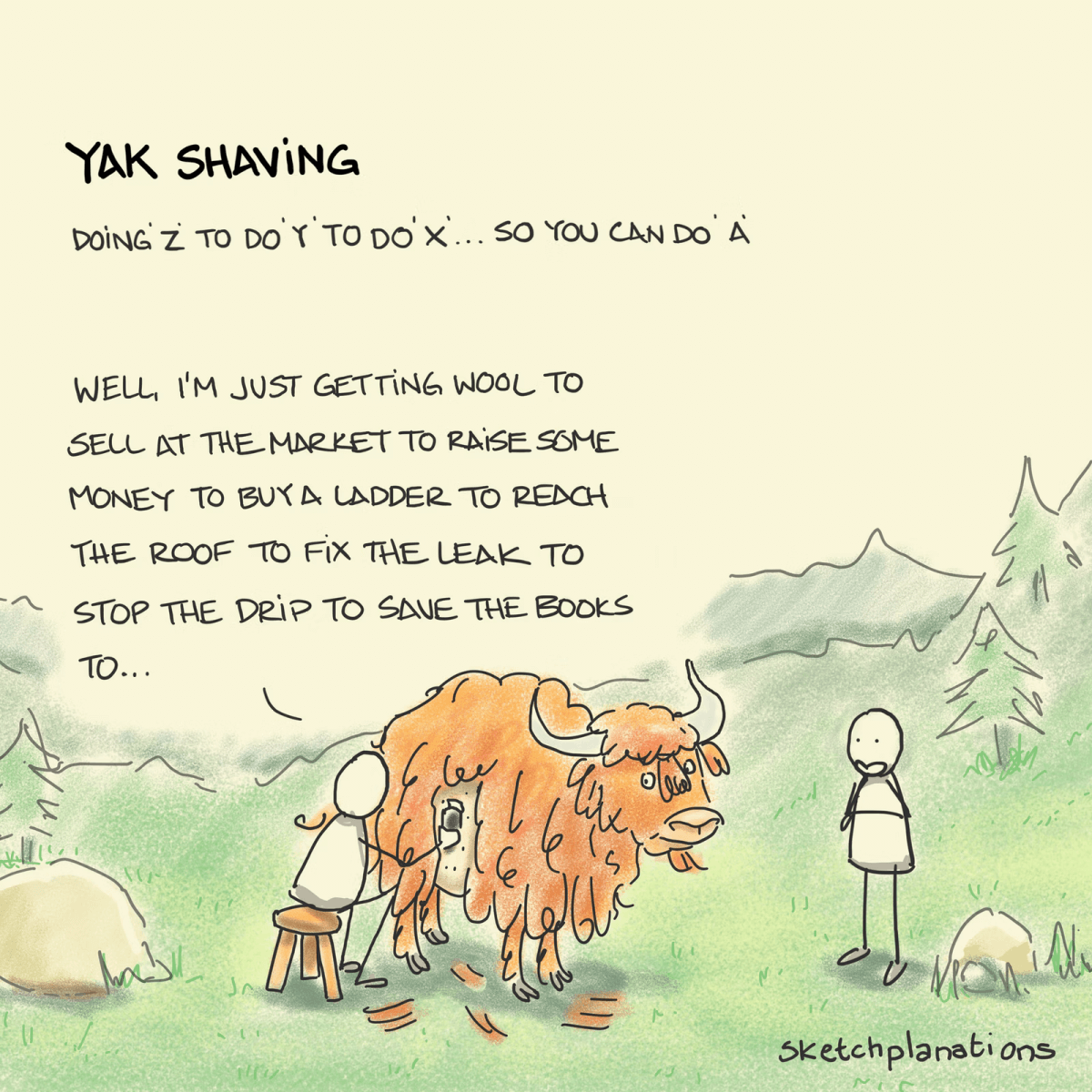
Yak shaving by the extremely talented Jonathan Hey at sketchplanations.com
Access for external team members is easier and safer because even if their network is compromised, threats will be blocked before they can do any damage.
For the DevOps team, it means a much smoother user experience. No more spending time setting up individual sessions for each DevOps service. And less time spent contacting their system administrator because something doesn’t work. ZTNA provides users with the necessary tools and connections to do their job, according to the defined access rights.
While ZTNA protects the actual product development from threat actors – which is, of course, business-critical – it also helps the project run smoother and faster. Using ZTNA makes the communication in a DevOps environment just as Agile as the project team.
Simply put, by adopting ZTNA into the DevOps workflows and tooling, teams can concentrate on securely connecting the right people to the right resources and workloads without any hardware, infrastructure, or upfront costs allowing teams to focus on productivity, not the limitations of their VPN.