Enclave Blog
Takes on network infrastructure, the state of security, and insights on the industry from the Enclave team.
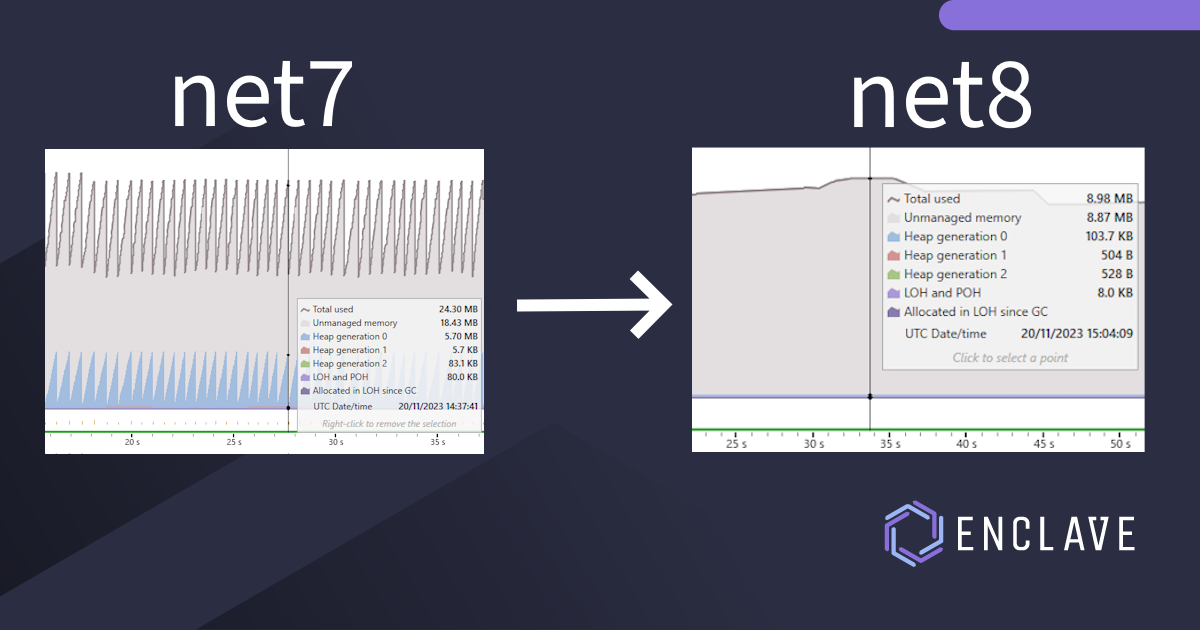
High Performance UDP sockets in .NET8
How we take advantage of improvements in UDP socket performance in .NET8
Enterprise Identity Providers and Enclave
Announcing support for Okta, Duo, JumpCloud and other OpenID Connect identity providers.
Enclave June 2023 Release
Announcing Active Hours, Auto Expiry, mobile user authentication and more!
Enclave & Weeve Partnership
Enclave & Weeve join forces to deliver secure connectivity and improved ROI for IoT deployments
Enclave Mobile release
Announcing the release of Enclave on Android and iOS.
Enclave Gateway Release
Use Enclave Gateway to route to devices that can't run Enclave, or even the entire internet!
Enclave June 2022 Release
Trust Requirements, Agent User Identity, Auto-dns on Linux, and more!
Terraform Support Has Landed
Good news everyone! Enclave now works with Terraform!
The state of Zero Trust Network Access
Zero Trust Network Access has a bright, but slightly opaque future. Here are our predictions for 2025.
VPN Servers are an Overcomplicated Security Liability
Users report significant performance and security problems
DevOps and ZTNA: The Ultimate Agility Enabler
DevOps is Agile, but gaining private access is not
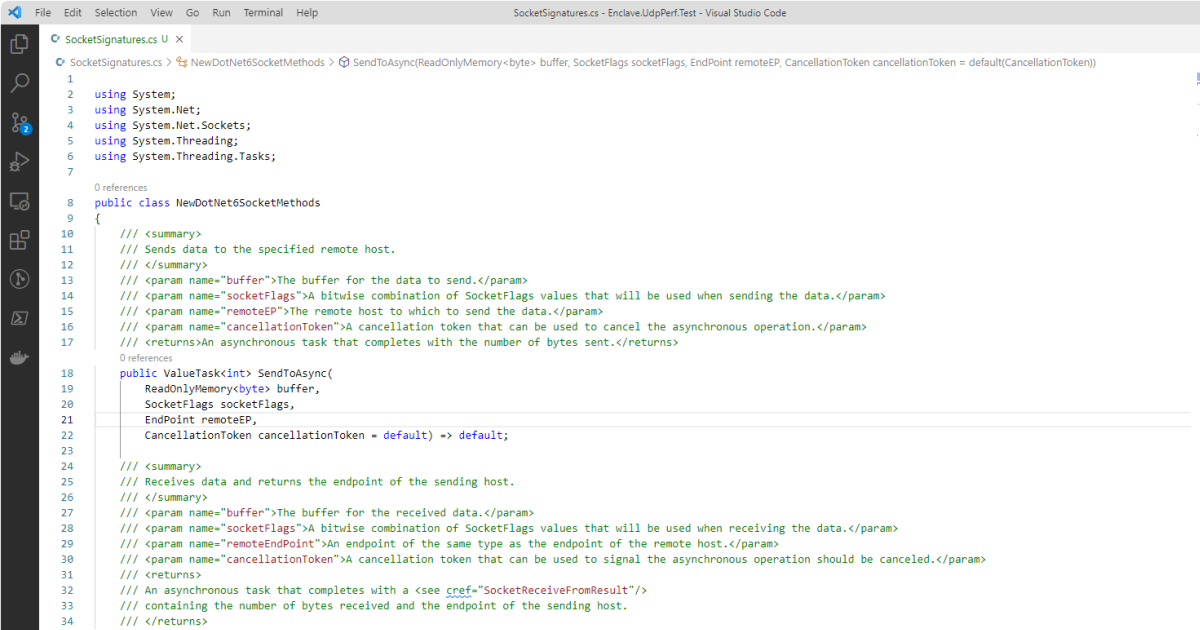
High Performance UDP sockets in .NET 6
How our socket code in Enclave squeezes the maximum performance out of UDP in .NET
Secure access to self-hosted GitLab
Without ingress traffic, opening ports or exposing your private servers to the public Internet.
Zero Trust sounds the death knell for VPN
VPN servers have outlived their usefulness.
Insecure networks prevent organizations from being agile and innovative
Unfortunately, such solutions can often become complex, difficult to manage and create vulnerability gaps.
Support for Single Sign-On
Enclave now supports Single Sign-On with Microsoft, Google and GitHub.
Enclave Networks closes $1M funding round
The investment comes as businesses continue to grapple with cybersecurity concerns around remote home working and managing multi-cloud environments
Linux, Cockpit And Enclave
Manage your Linux server and Enclave with Cockpit
Simple and Secure Remote Access
An easy and secure way to manage your own devices remotely with Enclave
Enclave November 2021 Release
Access Control Rules, Ephemeral systems and more!
Enclave joins NCSC for Startups
We’re very excited to announce that Enclave has been selected to join the NCSC for Startups programme.
High Performance UDP sockets in .NET 5
How our socket code in Enclave squeezes the maximum performance out of UDP in .NET