
We’ve just released a new version of Enclave with some features that we’re pretty excited about. These help to address a number of important use cases, and add a bunch of value for customers and partners!
I’ll take you through a summary here, but if you want any more information, don’t hesitate to get in touch!
No idea what Enclave is? We create “just works” private network connectivity between systems anywhere on the internet, without opening any of your firewalls, adding edge devices, or changing your infrastructure. We can replace your VPN with a simpler, better option that conforms to zero-trust principles. You can start a free trial at https://enclave.io.
Active Hours
A lot of network activity in organisations follows predictable work patterns. For example, a huge percentage of network connectivity typically happens between 9am and 5pm, Monday to Friday. Historically we’ve often defined connectivity that works 24/7, even though in reality connectivity outside the “active hours” for a given use case may be undesirable.
Imagine you have used Enclave to provide access to an on-prem AD environment, or indeed the whole corporate network, so that your employees can work from home or on the move.
If an employee has Always-On access to a server in your network via Enclave, and their laptop is stolen or left somewhere on a Friday, your employee may not notice until Monday, and you may not have a weekend IT team on hand to notice alerts from unusual user activity. This means an attacker may have the entire weekend to try brute-forcing passwords against your servers!
Or, for a few more examples:
- You have a contractor that only works two days a week, and shouldn’t have connectivity to company resources the rest of the time.
- You have a company policy forbidding overtime, and want to enforce it by blocking access outside of working hours.
- You have an out-of-hours support team in another time zone that shouldn’t be able to access your systems in regular hours.
- You run your backups every night at 1am, and don’t want anyone to have connectivity to your backup storage the rest of the time.
With the new Active Hours feature in Enclave policies, you can indicate that connectivity on a given policy is only available during the exact period the system/user should have connectivity. Not only does this reduce potential opportunities for misuse of policy, it allows you to get closer to the zero trust principles outlined in NIST and other regulatory requirements, because you can now include a time component in connectivity decision-making.
To use the new Active Hours feature, edit an Enclave Policy, and enable the feature. You can specify a start and end time, and which days of the week connectivity should be active.
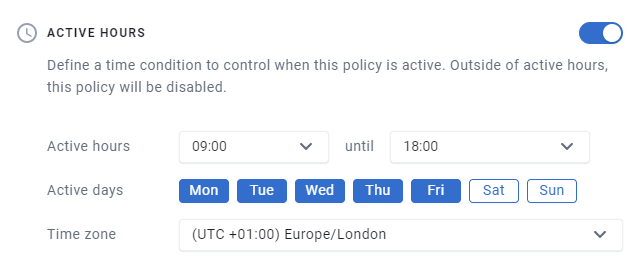
Our platform will take care of bringing connectivity up and down at the appropriate times, meaning you can rest assured that your users only have connectivity when they need it.
Auto Expiry
When a user needs to accomplish a task that occurs infrequently, modern security principles recommend that they only be given access to the required systems for the duration of their task, and lose that connectivity once their task is complete.
For example, if you have a user that needs to “break glass” into a production environment to retrieve logs, or a support engineer that needs to access a user laptop to progress a support issue, you want to make sure that they don’t retain that access for longer than is required.
It can be challenging to achieve this requirement without placing a significant burden on support and IT teams to correctly remove connectivity after the required period, especially when using legacy private connectivity solutions such as VPNs.
Luckily, we’ve added a new Auto Expiry feature to our platform to help with exactly this scenario!
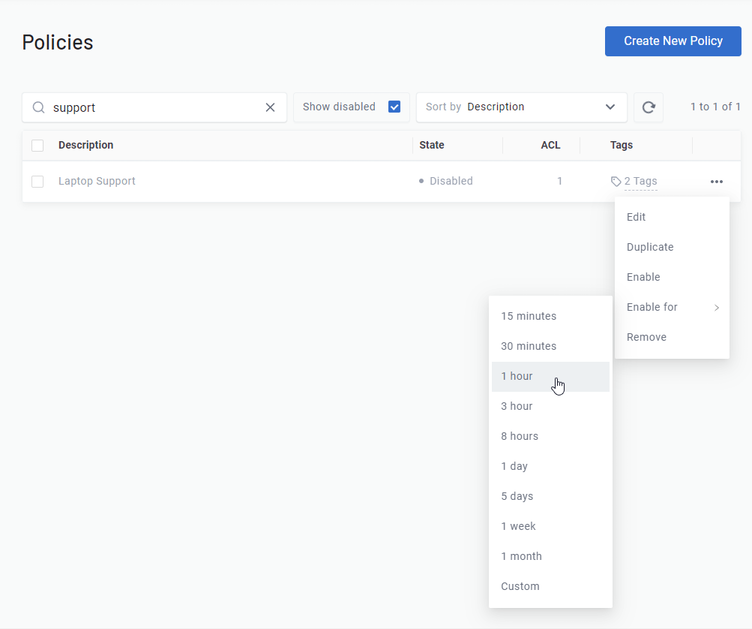
You can apply Auto Expiry to:
- Policies, when you want to expire a micro-segment of connectivity after a period of time,
- Systems, when you have an enrolled system that should lose access at the end of a defined period (for example, a contractor only onboarded for 6 months), and
- Enrolment keys, when you only want an enrolment key to be usable for a fixed task (for example, rolling out a series of desktops over the course of a day).
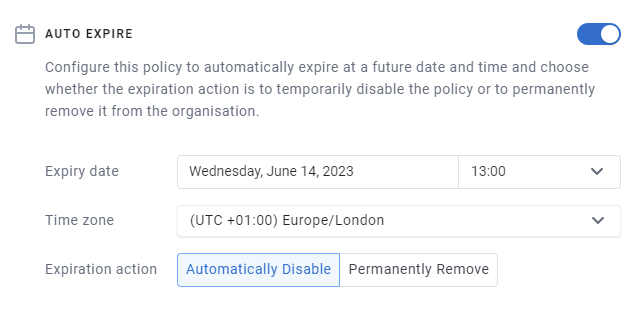
You can specify a custom point-in-time to end connectivity if the provided list of times don’t meet your needs; if doing so, you can also choose to permanently delete the selected item, as opposed to disabling it.
Mobile User Authentication
When we released support for mobile devices earlier this year, we had yet to add support for user authentication support on iOS and Android; I’m pleased to announce that we’ve now rolled this feature out in our mobile apps, so you can authenticate users connecting over Enclave from their mobile devices.
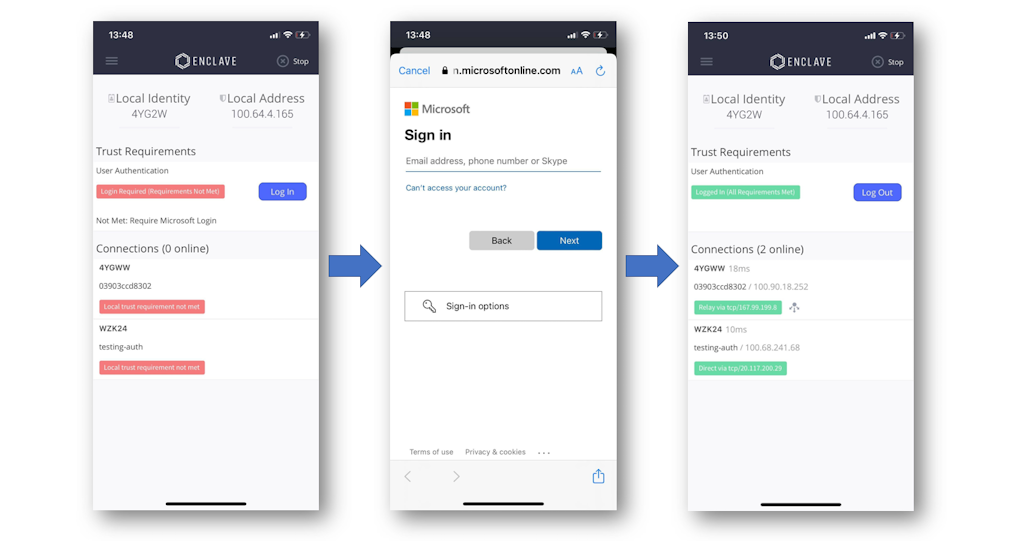
We support the same set of identity providers on mobile as on desktop, and if you have any AzureAD Conditional Access requirements that apply to mobile devices, those will apply.
Partner Focus: Switching Between Customers
At Enclave, one of our primary goals is making it easier for our partners and service providers to manage their customer networks, and reduce the time it takes to address support tickets.
A partner recently pointed out that a common use-case for them is for a support engineer’s workstation to be enrolled into each of their customer’s Enclave organisation, so they can connect to provide support as needed.
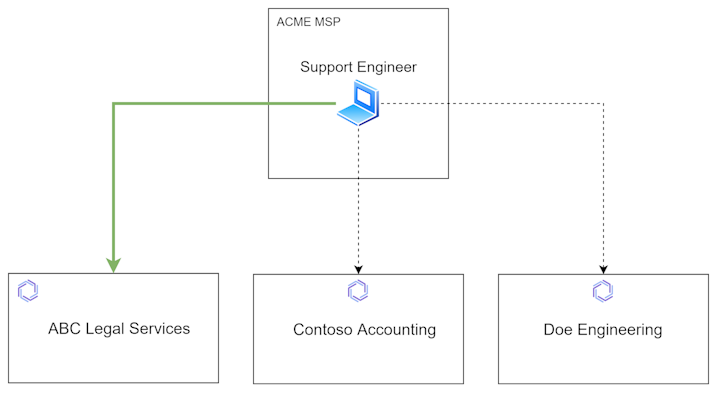
Only one customer’s systems should be reachable at once, but it’s useful to be able to switch easily between each of the available networks as focus moves from one customer to the next.
This Enclave release adds the ability to easily switch between multiple enrolled profiles, meaning a support engineer can change between customer networks in seconds, reducing the time required to address support tickets.
This change includes letting the Enclave tray application show the status of the currently running profile, not just the default profile, making it easy to see exactly what is going on, whichever customer you are managing.
Wrapping Up
There’s a lot of great new features available, and we continue to strive to make our partners and customers lives easier; if you’ve got any questions about these new features, feel free to contact us and we can discuss how they can assist with your specific use case.