Is your business relying on VPN servers to protect customer infrastructure?
For many, the idea of VPN servers guarding customer networks gives them chills, conjuring up images of sitting ducks.
In fact, using VPN servers for remote access in 2024 is certainly no longer the most compelling part of your service wrap, especially when customers are subject to a constant stream of news about information disclosure, credential stuffing, phishing attacks, ransomware, zero-day exploits and backdoored accounts in VPN products.
We all know that VPN servers have been increasingly under the spotlight since COVID-19 forced the world to embrace remote working, and then again in 2021 as hackers shutdown the Colonial Oil Pipeline in the U.S. after gaining VPN access, but the humble VPN is facing a much larger threat now:
An extinction event, driven by Zero Trust.
As an MSP, you no doubt understand the importance of providing secure and reliable network access to your customers and the role it plays in maintaining their trust (and your reputation), and while the Zero Trust movement might seem daunting, modernising your technology stack early can help to position your business for growth as the world begins to transition away from “trust but verify” security towards “never trust, always verify”.
In this article we’ll look at Zero Trust from an MSP’s perspective. We’ll provide suggestions on how to discuss Zero Trust with your customers, explore strategic benefits for your business, clarify the connection between philosophy and practice, and offer some practical ideas about how to get started on your Zero Trust journey in small, incremental steps.
Zero Trust for your customers
As an MSP, it’s essential to communicate the value of Zero Trust in a way that resonates with your customers. Let’s break down why Zero Trust is such a game-changer for them.
Firstly, it’s important to understand that the trend towards Zero Trust first gained serious momentum after the U.S. government introduced mandatory requirements for federal agencies to adopt it in the wake of cyber-attacks against critical infrastructure on the 6th of May, 2021.
Six days later, the Biden Administration issued the Executive Order mandating the adoption of Zero Trust. 11 days later the British National Cyber Security Centre (NCSC) followed suit publishing architecture guidance
Almost overnight, a new standard in cybersecurity practices was ratified, and as the saying goes, the trend is your friend.
We’ll approach Zero Trust from the most obvious angle first, enhanced security. Zero Trust isn’t just another security measure; it’s a tactical fortress against a wide range of threats, from ransomware, malware and credential theft, to brute force attacks and phishing and more.
Improvements in security posture can also help to reduce risk, and Zero Trust plays a pivotal role here. It’s not just about preventing breaches; it’s about safeguarding your customer reputation, data and finances, and maintaining tight control over access drastically lowers the chances of breaches, which is a top concern for many businesses.
Zero Trust also eases the compliance journey, whether that’s Cyber Essentials in the UK, NIST or HIPAA in the U.S. or others; because it aligns perfectly with regulatory requirements like strict access control and the principle of least privilege access.
Lastly, don’t forget about improved customer experience. Your customers aren’t just getting more secure networks; they’re getting better reliability and fewer interruptions due to security issues. A seamless customer experience is worth its weight in gold for MSP reputation and customer retention.
Zero Trust for you
The 2023 SMB Threat report from Huntress shows 65% of attacks on small and medium businesses leveraged RMM tools to gain unauthorized access to victim systems. Crucial for MSP operations, but increasingly under attack, the trend of threat actors targeting RMM software poses a threat to your infrastructure and customer security. By adopting Zero Trust, every interaction with your RMM platform is authenticated and authorized, significantly strengthening your defence against unauthorized access and breaches.
This is where you can leverage your position as an MSP with not-for-resale (NFR) licences. Not only an excellent opportunity to learn about ZTNA products, but simultaneously deploy state of the art protections without additional cost around the crown jewels of your business: access to the RMM.
More than that, getting the right mix of vendors into your technology stack is also going to dramatically simplify network management, cutting through the complexity of traditional security tooling, and instead focusing on what’s crucial — strict authentication and minimal access.
Why now
We’ve already mentioned security vulnerabilities undermining the traditional security perimeter exacerbated by the shift towards work-from-home arrangements and COVID-19; but there’s also time-sensitive reason to adopt Zero Trust now: competitive advantage.
Today, Zero Trust is a market differentiator, not a standard customer expectation. In the competitive MSP landscape, adopting advanced security measures like Zero Trust can set your services apart from others. While Zero Trust is gaining attention, it’s not yet ubiquitous, meaning that implementing it now can give you a leading edge. Strong differentiation can be a significant factor in attracting new customers who are looking for top-tier security, as well an edge in retaining existing customers, offering them the latest in network security and positioning your business as a forward-thinking and security-conscious early adopter of new technologies.
Think of Zero Trust as an investment in your business’s future, not just a security protocol. By implementing it, you’re not only enhancing your security posture but also building a foundation for growth, reliability, and customer confidence.
Recognising this, let’s delve into the philosophy and practice of Zero Trust.
Zero Trust Security Model
Many readers may already know that Zero Trust is an approach, a mindset: “Never Trust, Always Verify” rather than a product. But since part of a Zero Trust strategy means replacing the VPN, we need new products to help implement it, and not just for the network. You’ll need to consider how to operationalise the Zero Trust Security Model across the entire IT infrastructure spanning users, devices, networks, applications and data.
In this article however we’ll focus on VPN servers and their replacement, Zero Trust Network Access, as we explore Zero Trust.
When we talk about security models, we’re simply referring to any theoretical framework which describes how security should be implemented and enforced.
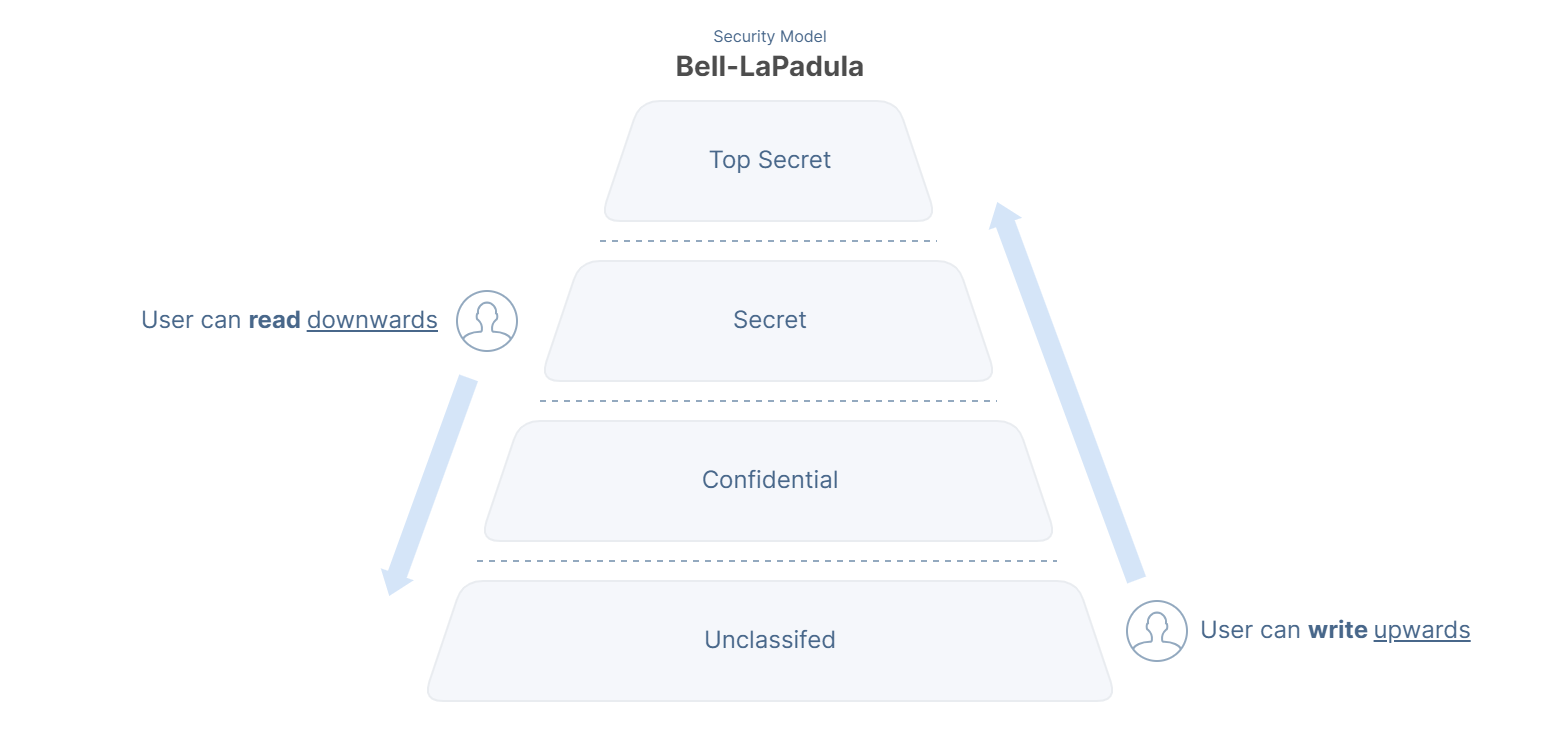
For example, Bell-LaPadula while not directly related to Zero Trust, is a classic example of a simple security model used in government and military applications. The key principles — a user may “write up, but not down” and a user may “read down, but not up”, depending on security clearance.
The Zero Trust Security Model however is replacing something much older. The VPN server is based on the ancient and de-facto concept of “castle and moat” security which wraps a hard shell around your protected assets but leaves a squishy, trusted core at the center.
This “perimeter-based” security model as it’s also known was popularised for use online in the 1990s and remains in widespread use today, in no small part because of the sheer volume of private access tooling that’s been built with this model in mind.
Principles
In contrast, the Zero Trust Security Model is modern approach to online security that combines several existing and well-established principles under a guiding philosophy which promotes the removal of any implicit trust.
The Zero Trust Security Model principles act as rules and guidelines to direct our actions and decision making, telling us how to “never trust, and always verify”. While Zero Trust as a concept is still gaining popularity, the key principles underpinning it should be quite familiar to most security-aware IT practitioners.
In fact, an easy way to think about Zero Trust is as an amalgamation of pre-existing, robust security ideas tied together under the philosophy of “Never Trust, Always Verify”, complimented by a range of emerging products and new tools designed and built to be sympathetic to this model.
-
Continuous verification: Risk is not static, it changes continuously, the objective of this principle is to be constantly re-evaluating the security posture of all devices and users, revoking access as necessary if confidence lowers to ensure all resources are trusted, secure and compliant to company policy.
-
Verify explicitly: Always authenticate and authorize access based on all available data points. The objective of this principle is to ensure there is no implicit trust, even for something that’s already in our environment. The idea is to ensure every access is authenticated and authorized rigorously and precisely, using all available data, including user identity, location, device health, and other contextual factors to reduce the risk of unauthorized access.
-
Least privilege access: Limit user access with just-in-time and just-enough-access. The objective of this philosophy is to minimise security risks by providing only the required access, exactly when it’s needed, and only for as long as is necessary to limit the potential for unauthorized access or damage if a user’s credentials are compromised.
-
Micro-segmentation: Break up security perimeters into small zones to maintain separate access for separate parts of the network. The objective of this philosophy is to prevent over-permissioned access and reduce the attack surface area by ensuring that systems and resources within one segment are isolated from others.
-
Prevent lateral movement: Like Micro-segmentation, this philosophy aims to confine security threats to a limited area but focuses on ensuring strategies and controls are in place to stop an attacker from moving around within the network after they have gained access.
-
Assume breach: Operate under the assumption that breaches have occurred or will occur. Continue to increase security to ensure our designs are in place to contain a breach. The objective of this philosophy is to continuously work to reduce the blast radius of an incident.
-
Automate security actions: Prefer the use of automated solutions to detect and respond to security incidents to reduce the need for manual intervention. The objective of this philosophy is to improve reaction times and consistency, quickly responding to threats and policy violations.
-
End-to-end encryption: Ensure data is encrypted not only in transit, but also at rest. The objective of this philosophy is to protect data integrity and confidentiality at all stages to reduce the risk of data breaches or unauthorised access.
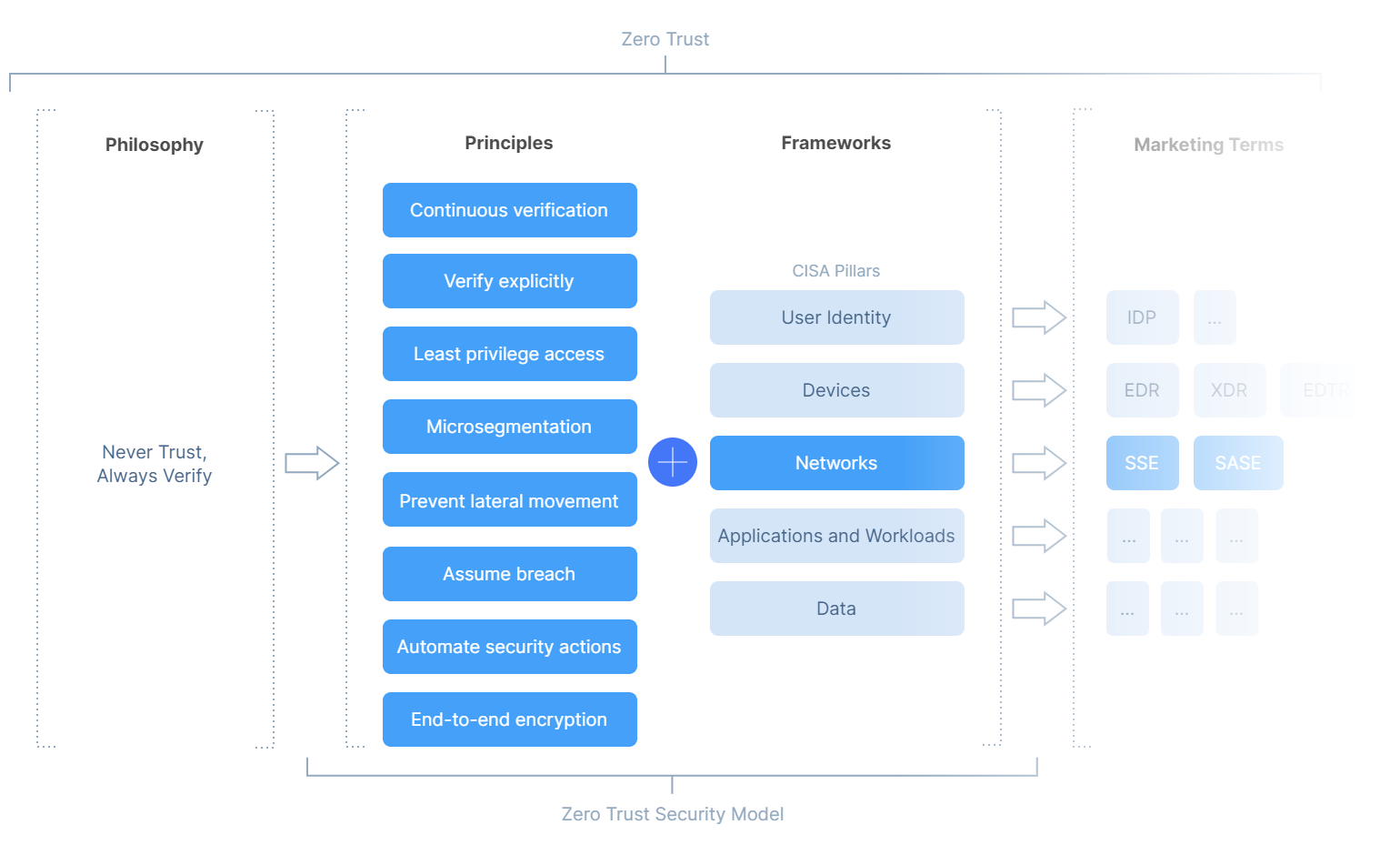
Notice that Zero Trust Security Model — or set of Principles — which we’ve looked at so far, is book-ended on the left in our diagram above by Philosophy: The Zero Trust mindset, and on the right by Frameworks.
Frameworks
Frameworks are vital because they help merge the theory (philosophy and principles) with the technology and business resources, telling us exactly where, and how to apply the principles.
The most widely recognised frameworks today are those published by Government entities listed above. These frameworks primarily focus on delivering guidance to Federal or Government agencies, shaping their transition towards Zero Trust.
- National Institute of Standards and Technology (NIST) — SP 800-207, Zero Trust Architecture
- National Cyber Security Centre (NCSC) — Zero Trust Architecture Design Principles
- Department of Defense (DoD) — Zero Trust Reference Architecture
- Cybersecurity and Infrastructure Security Agency (CISA) — Zero Trust Maturity Model
In the same way that guidance for which vehicle to drive should be tailored to circumstance, requirements and means, there are differences between each of the publications, and this is where Zero Trust starts to get complicated.
Even at a high level, comparing NIST’s Zero Trust Tenets and NCSC’s Zero Trust Principles, for example; while broadly similar, the foundational points could easily take implementors in different directions.
| NIST Zero Trust Tenets | NCSC Zero Trust Principles |
|---|---|
| 1. All data sources and computing services are resources. | 1. Know your architecture including users, devices, services, and data. |
| 2. No trust is automatically assumed based on network location. | 2. Know your User, Service and Device identities. |
| 3. Access to resources is granted on a per-session basis, following the least privilege principle. | 3. Know the health of your users, devices and services. |
| 4. Access to resources is determined by dynamic policy. | 4. Use policies to authorise requests. |
| 5. Continuous diagnostics and mitigation (CDM) of all devices and applications. | 5. Authenticate & Authorise everywhere. |
| 6. Use of ICAM and asset management systems for reauthentication and reauthorization. | 6. Focus your monitoring on devices and services. |
| 7. Collect extensive information about the state of assets, network infrastructure, and communications. | 7. Don’t trust any network, including your own. |
| - | 8. Choose services designed for zero trust. |
It’s important to remember much of the Zero Trust guidance was drafted with some of the world’s largest organisations mind. So as an MSP, it’s important to right-size your approach to Zero Trust and think of it as a maturity journey.
For this reason, we’ll use the Maturity Model published by CISA as our guide. While it’s only one of many paths available to support the transition to Zero Trust, it’s particularly useful for small and mid-size organisations precisely because the authors recognise the need to approach Zero Trust as a journey.
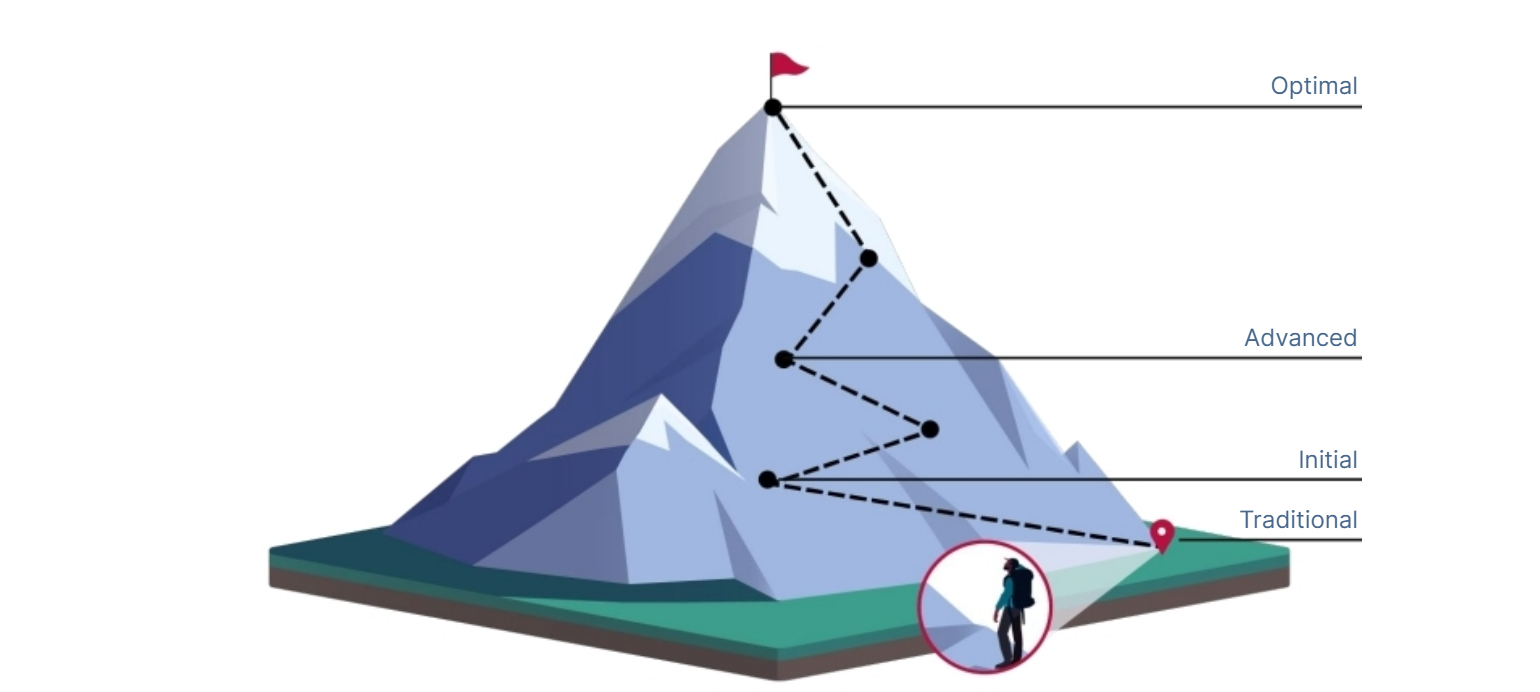
Image Source: "Zero Trust Maturity Model V2"
Cybersecurity & Infrastructure Security Agency (CISA), April 2023, Page 8, Source
CISA’s maturity model demonstrates how incremental advancements can be made over time, starting from current security best practice and moving forward.
Their model outlines a “gradient” of Zero Trust maturity across five distinct pillars, in which minor advancements can be made over time towards optimisation. Each pillar can progress at its own pace and may progress more quickly than others.
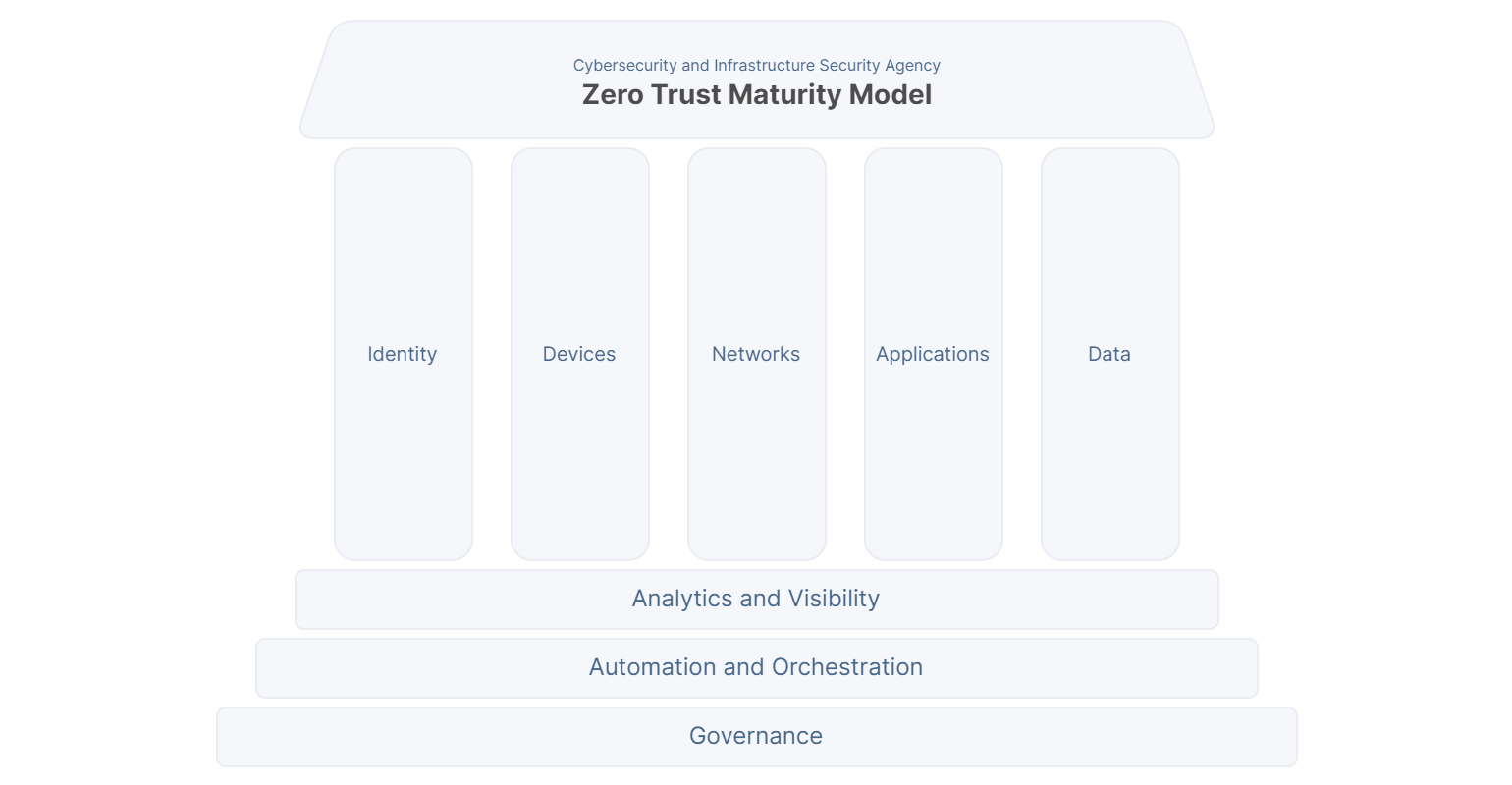
The five pillars are:
- User Identity: The ability to uniquely describe a user or resource.
- Devices: Any asset (including hardware, software, firmware, servers, desktop and laptop machines, printers, mobile phones, IoT devices, networking equipment etc.) that can connect to a network.
- Networks: Internal networks, wireless and on-premise, Cloud, home workers, B2B partnerships.
- Applications and Workloads: Programs, services and workloads that execute on-premises, on mobile devices, and in cloud environments.
- Data: All structured and unstructured files and fragments that reside or have resided in systems, devices, networks, applications, databases, infrastructure, and backups (including on-premises and virtual environments) as well as the associated metadata.
Each pillar also includes cross-cutting themes which re-enforce key Zero Trust principles:
- Visibility and Analytics: Continuous monitoring and analysis of logs and events.
- Automation and Orchestration: Implementing automated responses to security events.
- Governance: Policy-based controls and completeness of coverage.
The important thing to realise as an MSP is that Zero Trust maturity will be different for every business and customer, and not all journeys will, nor should look the same or progress at the same rate.
Marketing Terms
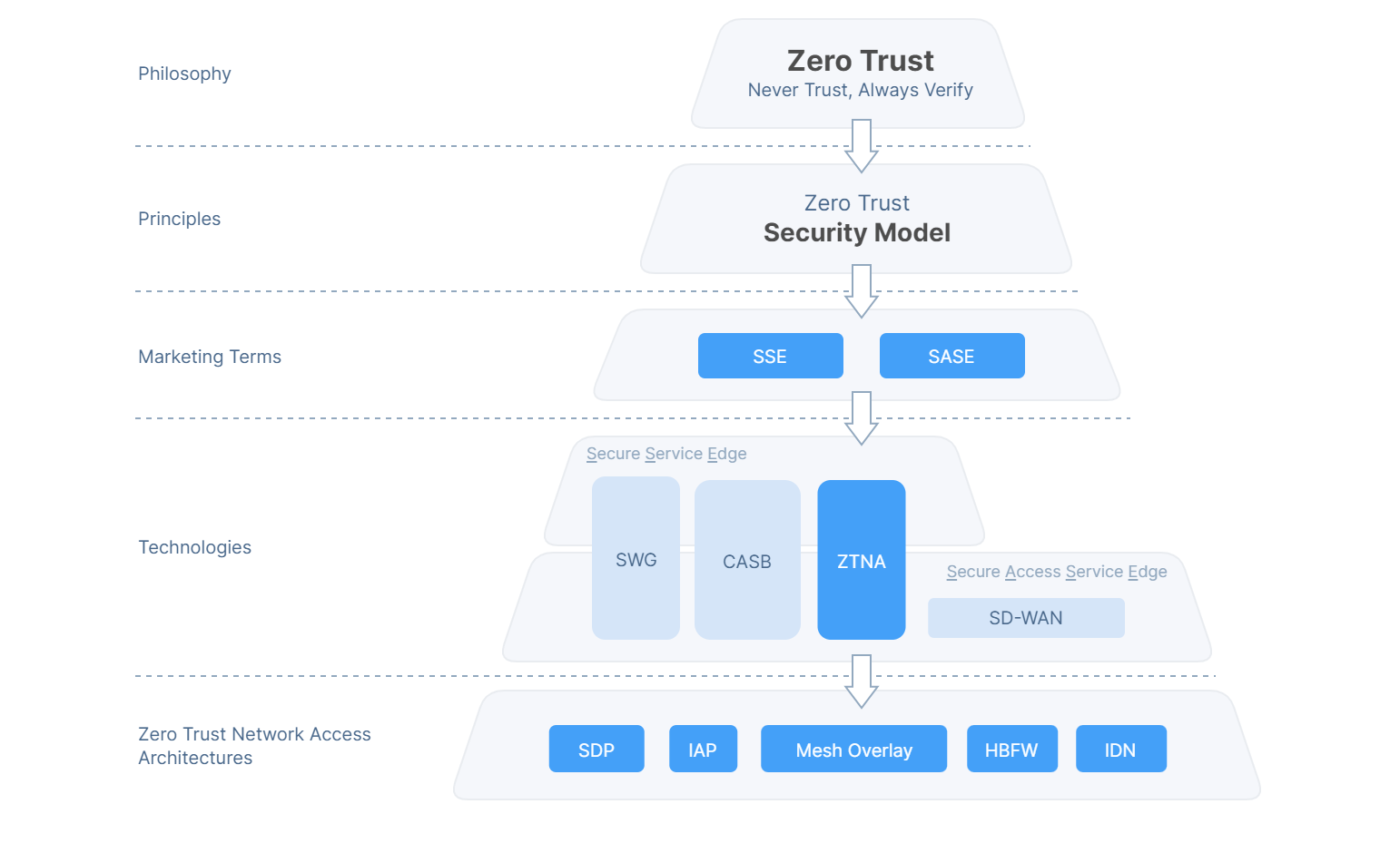
Before reaching into Zero Trust Network Access technology and architecture, it can be helpful to step back and understand some of the marketing terms which have emerged, encircling the technologies and what they mean.
Other marketing terms like Next-Generation Firewalls, or EDR, MDR and XDR, while not connected to Zero Trust, do all represent well-intentioned attempts to find convenient terms to differentiate products from one another as the market shifts and new business models, capabilities, technologies and architectures emerge over time.
Zero Trust is no different. Market analysts like Gartner and Forester regularly coin new terms, trying and help consumers make sense of fundamental shifts.
Gartner coined the broad term of “Secure Access Service Edge” (SASE) in 2019, and then “Secure Service Edge” (SSE) in 2021 as a subset of SASE. Both terms refer to packaging complimentary technologies like Secure Web Gateway (SWG), Cloud Access Security Broker (CASB) and ZTNA together into single a solution and delivering it from the cloud, in alignment with Zero Trust principles.
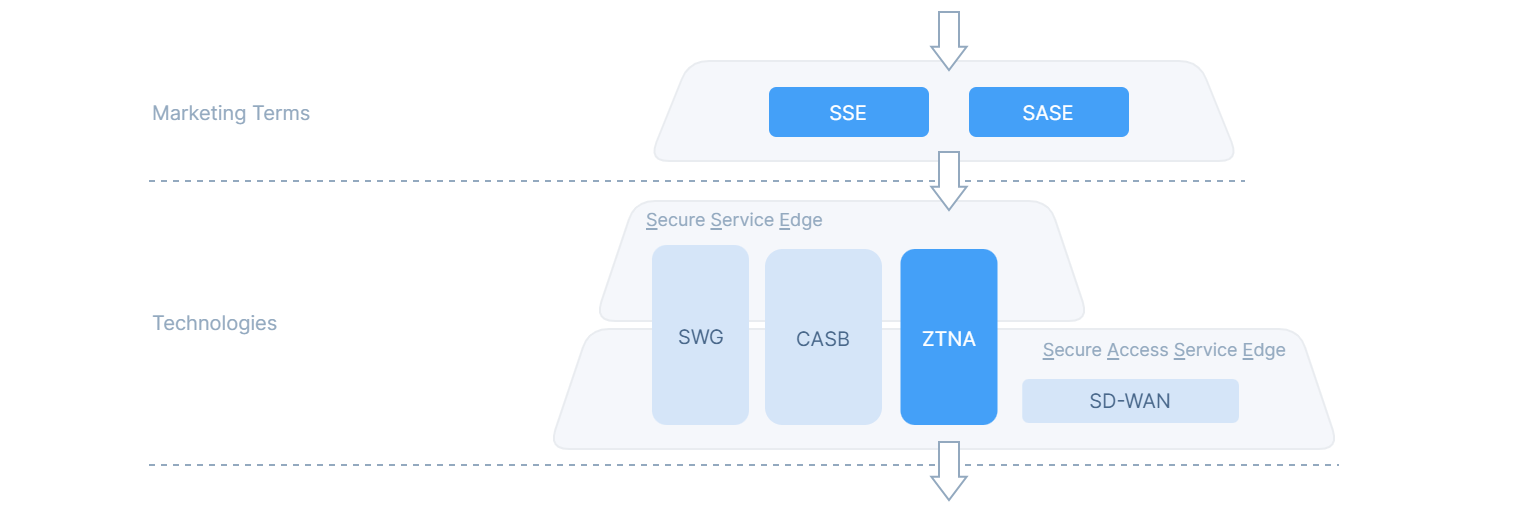
One of the challenges with this dynamic, is that as soon as one vendor then brands themselves as SASE or SSE, others feel compelled to do the same, which can dilute the overall market value.
When Gartner defined the term SASE, SD-WAN (a technology that manages and optimizes wide area networks) was still a relatively popular concept, but as Zero Trust Network Access technologies matured, SD-WAN has become less relevant for many organisations, leading Gartner to recognise the shift with another new term, SSE.
In our experience at Enclave Networks, most MSPs will deploy a combination of SWG and ZTNA for their customers. CASB is less common in customers serviced by MSPs and SD-WAN is becoming increasingly irrelevant for all but enterprise customers as many ZTNA implementations already provide the most direct and efficient routing between users and applications connected by the public Internet.
Zero Trust Network Access
We’ve traced the outline of Zero Trust from philosophy and principles to frameworks and marketing terms.
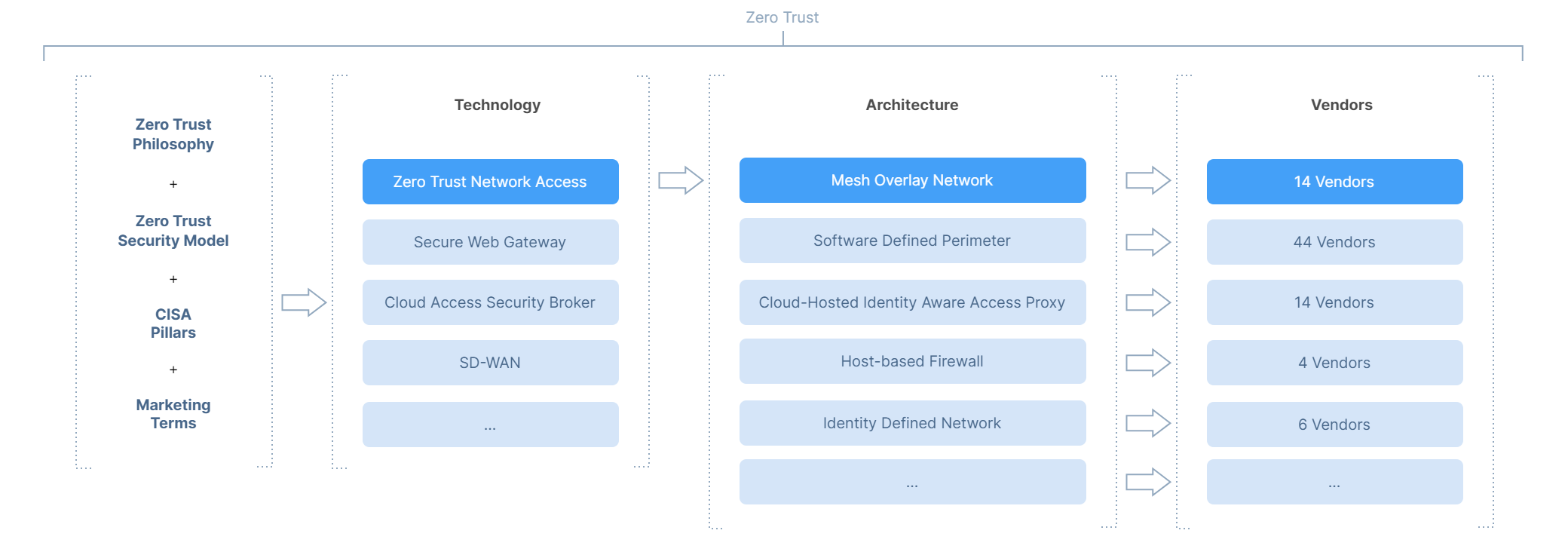
As you can see from the diagram below, each CISA Pillar can be serviced by one or more technologies:
-
Secure Web Gateway (SWG): Filtering unwanted ads/malware and other threats from user-initiated web/internet traffic.
-
Cloud Access Security Broker: Intermediary service deployed between users and cloud service providers ensure compliance, visibility and data security.
-
Zero Trust Network Access: Corporate VPN replacement. Secure access to applications and services based on identity verification, without relying on traditional network-based perimeter security.
-
SD-WAN: Manages and optimizes network traffic across wide area networks (WAN) links to automatically determine the most effective way to route traffic to and from branch offices and data centers.
Each technology in turn be implemented using one of several architectural approaches. For example, one vendor may decide to deliver their solution entirely via the Cloud, another may elect to build appliances for the MSP to deploy into the customer’s network.
How ZTNA works
Regardless of the architecture, the main characteristics of any Zero Trust Network Access solution, as defined by Gartner are:
- Applications are hidden from discovery, no public visibility.
- Access is restricted via a trust broker.
- The trust broker verifies the identity, context, and policy.
- Lateral movement in the network is prohibited.
- There is a reduced surface area available for attack.
As you’d expect, Zero Trust Network Access (ZTNA) combines Zero Trust principles with the network, forcing products to assume no one, whether inside or outside the network can be trusted without thorough authentication and authorization.
Unlike VPNs which over-permission users onto the network, ZTNA never assumes trust by default. Instead, users are required to be authenticated and authorized every time they access resources.
ZTNA focuses on granting users access only to the specific resources they need, rather than full network access. This means that each access is verified independently, regardless of whether the user has been authenticated and authorized before.
To achieve ZTNA, several technical elements are involved:
- First, a robust multi-factor authentication (not SMS-based) is needed to identify, authenticate, and authorise users.
- Second, context-based access control ensures that only authorised systems and resources are visible to the user, limiting privileges.
- Third, device posture checks, such as ensuring the security of the machine, are conducted before granting access. Which may include checks like verifying if an endpoint detection and response (EDR) system is running.
ZTNA goes beyond authentication, requiring continuous monitoring and evaluation of identity, context, and posture. Any changes in these factors can lead to access being revoked as necessary, ensuring a dynamic and adaptive approach to security.
Implementations and the architecture of ZTNA products varies among vendors, but all involve a trust broker, which can be either a local network device or cloud delivered service.
The trust broker is responsible for authenticating and authorizing access, as well as continuously evaluating identity, context, and posture. The trust broker is part of the control plane, which controls the management and intelligence of ZTNA policies, while the data plane handles the enforcement and establishes connections between resources.
It’s important to note that the specific implementation of ZTNA can differ between vendors, so the technology used may vary. However, the key principles of Zero Trust, such as continuous authentication and authorization, are essential regardless of the specific implementation.
One of the key differences between architectures is whether customer traffic moves via a cloud-based data plane and the vendors network, or the customer retains data sovereignty.
There are several architectures available today. Each architecture has unique strengths, trade-offs, and weaknesses and of course vendor specific traits (like how the product is deployed, configured, supported and priced), but an understanding of the different roads which can lead to ZTNA can help MSPs evaluate the right vendors for their needs.
The team at Enclave Networks provides a solution based on a “Mesh Overlay Network”, but we also maintain a curated, impartial and open-source directory of ZTNA vendors and architectures for the community as a whole benefit from honest, impartial, and open knowledge at https://zerotrustnetworkaccess.info/ which tracks about 90 different vendors at the time of writing.
How to get started with Zero Trust
As an MSP, getting started with Zero Trust is an exercise in the art of right sizing both effort and tooling, but you might be surprised by how much you already have in place.
Step 1 — Identity
Put an Identity Provider (IdP) into your customer’s organisation. It’s the foundation of any Zero Trust journey and must be your first step. Consider Microsoft’s Entra ID, Okta, Duo or many others. If your customer is using on-premise Active Directory, now is the time to synchronise user identities between local and cloud directories with Azure AD Connect. Remember: One user, one login and one Identity Provider.
- Establish and manage corporate identities with a single Identity Provider.
- Enforce Multi-Factor Authentication (MFA) across all applications.
Step 2 — Devices
Devices may be company-owned, bring-your-own-device (BYOD) property of employees, or owned by partners, or visitors. Start with company-owned devices registered in your RMM.
- Create an inventory of all corporate devices using your RMM platform.
- Implement endpoint management across all corporate devices.
- Safeguard these devices from threats by applying Endpoint Detection and Response (EDR) or Endpoint Protection Platform (EPP).
Step 3 — Networks
Your focus here is to create a secure foundation for your customer to do business. Think about network access and the types of traffic patterns your customer needs. Does the customer require private access to on-premise, cloud or partner resources (like privately addressable devices, non-browser apps, SSH, RDP, SMB, thick clients)? If so, consider deploying a ZTNA solution.
What about private access to trusted SaaS applications, is access to SaaS applications locked down to prevent unauthorised login attempts? If not, consider again deploying ZTNA, or use a CASB solution if your customer needs more control over access and auditing.
- Employ DNS filtering or Secure Web Gateways (SWGs) with SSL/TLS inspection to block harmful Internet-based threats.
- Deploy ZTNA or CASB according to your customer’s traffic patterns.
- Segment each user’s network access to control and restrict internal movement.
- Close all inbound ports that are open to either the Internet or LAN for application delivery.
- Integrate any tooling you deploy with your RMM and IdP solutions.
- Ensure company data is encrypted when in motion.
If there’s a VPN server, replace it.
For the purposes of this guide, we’ve assumed that as an MSP you’re not intentionally managing publicly addressable applications beyond static brochureware websites for your customer. Removing implicit trust from software development and deployment pipelines introduces many more touch points for Zero Trust principles, complicates the customer’s journey beyond the scope of this guide.
Step 4 — Applications
- Enable DMARC, DKIM and SPF on customer domain names.
- Monitor inbound emails and filter out phishing attempts.
- Inventory all corporate applications and ensure appropriate access controls are enforced with ZTNA and IdP integration.
Step 5 — Data
- Ensure data-at-rest is encrypted on all devices using whole disk encryption (available in all modern operating systems).
- Ensure access to data is appropriately user-permissioned and accesses are recorded.
- Consider whether your customer requires ransomware protection, it may be part of your EDR or EPP solution.
Next Steps
Create a Zero Trust dialogue with your customers.
After setting up the initial technologies for Zero Trust, consider the scale of deployment, automation level, and the unique context of each customer. This foundational phase can be just the beginning. The direction to take next should be shaped by discussions specific to each customer’s risk profile, their willingness to invest further, potential benefits and cost considerations.
Maintain a steady state
After implementing the initial technologies, your goal might simply be to enter a “steady state” with each customer. The key is to recognise that like anything else, over-investing can lead to diminishing returns and create fatigue. Your customer might feel that their Zero Trust journey is as mature as it needs to be.
At this stage, you’ve tailored the Zero Trust approach to suit their immediate requirements, which allows you to transition into a steady-state mode of operation for the customer.
During a steady-state phase, your role could involve providing ongoing management, optimising how visibility and analytics capabilities are used with continuous monitoring to analyse logs & events to enforce policy and automate security responses. Steady state also an opportunity to streamline your own management of the customer’s environment through automations, which can reduce time demands and increase the efficiency in your own service desk operations.
Quarterly Business Reviews are a great time to discuss the value that your solution brings your customers and ideally where you’re jointly reassessing whether the current level of Zero Trust maturity is still appropriate as their businesses grows and adapts to new challenges and security risks.
Grow your customer’s Zero Trust capabilities
Explore your customers’ aspirations and use the CISA maturity model help them to understand not only what’s been achieved, but also what’s possible together and how it aligns with their security goals.
For example, is customer using phishing-resistant MFA like FIDO2 or PIV? Is Identity and Network tooling integrated, identifying risk in real-time and dynamically adjusting access? How narrow is the scope of each granted access? Is data loss prevention relevant to you customer?
Questions to ask ZTNA vendors
Here we suggest a set of questions you should ask when considering a Zero Trust Network Access solution.
-
Coverage and Scalability: “Does your product provide comprehensive coverage for all types of network traffic (North-South and East-West)? How will it adapt to our range of customer needs and future expansions?”
-
IP Address Change Management: “In case of an IP address alteration in workloads, what is the required management overhead?”
-
Onboarding Process for New Sites: “What is the process for integrating a new site or location? Please detail the deployment requirements, lead times, management involvement, and costs.”
-
Business Model Alignment: “Does your business model align with our operational structure as an MSP, particularly regarding pricing models, bulk purchasing requirements and sector discounts? Do you offer Not-for-Resale licenses for internal deployment and testing purposes?”
-
Technical Support Responsiveness: “Can you describe the responsiveness and availability of your technical support, including the use of platforms like Slack or Discord for real-time assistance?”
-
Integration with RMM and PSA Tools: “How does your product integrate with existing Remote Monitoring and Management (RMM) and Professional Services Automation (PSA) tools?”
-
Incremental Deployment Capability: “Is it possible to implement your solution incrementally across our network? Does it require rip-and-replace or can it co-exist with current technologies? Does the MSP need to deploy hardware or appliances into the customer environment?”
-
Trial Period Availability: “Do you offer a trial period for your product to assess its suitability for our needs?”
-
Usage Limitations: “Are there any scenarios or environments where your product cannot be deployed or may not function optimally?”
-
Acknowledgment of Solution Limitations: “What do you consider to be the weakest aspect of your solution, and how open are you to feedback and improvements in these areas?”
-
Transparency in Platform Uptime: “Do you publicly disclose your platform’s uptime statistics and availability in real-time? If not, can you explain why?”
We hope you found this guide useful. If you have comments or suggestions, please write to team@enclave.io. Originally published at https://enclave.io/learn/zero-trust/ztna/msp-guide-to-ztna January 25, 2024.
