
Linux, Cockpit And Enclave
With my prior blog post about using Enclave to control your homelab servers, I made a passing mention to Cockpit. Now I’ll be honest I’d not heard about Cockpit until I started looking into moving my home media server over to Linux (I use Fedora Server). With some investigation it seemed that Cockpit was near enough perfect for what I wanted to do: manage my Linux server’s local storage and updates from a slick UI. Not to mention error logging!
For those who don’t know, Cockpit is web-based a management portal for Linux servers, developed in conjunction with RedHat Linux. It’s incredibly powerful; letting you manage near enough everything about the server through a web portal, and if you can’t do it through the web portal, Cockpit gives you access to a terminal in the browser too, so no need to SSH into your box. Oh and obviously given the topic of this blog post there are plug-ins!
So… plug-ins?
Knowing Cockpit supports plug-ins, my first question was: how do I make one for Enclave? To my surprise it was fairly simple. All you need is a manifest.json file, an index.html file and an index.js file. That’s it. You now have a plug-in.
Well not quite, you need do some supporting code, but that’s the overall structure. To use your newly created plug-in you’ll need to place the files in /home/[username]/.local/share/cockpit/[pluginName]. Now that’s done, refreshing the Cockpit UI in the browser will show your newly created plug-in on the left-hand menu.
Psst we’ve made it open source you can find it here!
How does the plug-in work?
The main functionality of the Enclave plug-in for Cockpit is based on the Enclave command-line interface. Enclave offers a --json modifier for most CLI commands, so I’ve made the plug-in call enclave status --json to get a structured document representing the status of the Enclave agent.
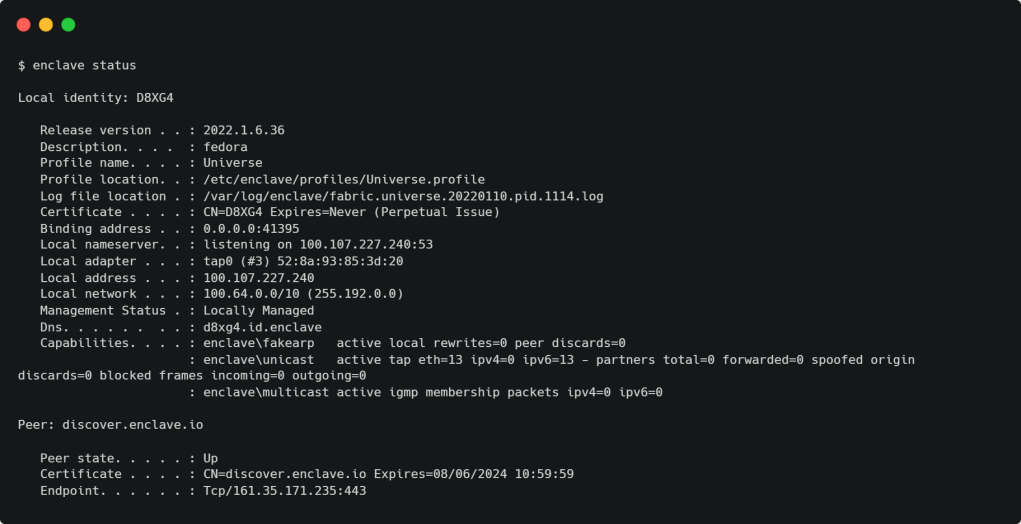
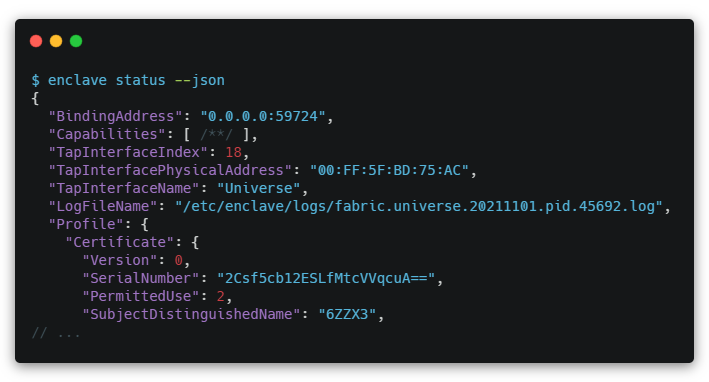
Cockpit has a useful set of tools for invoking commands and capturing what they write to stdout. The most notable of those is the cockpit.spawn method provided by cockpit.js. I used it like this:
1
2
3
4
5
6
7
8
9
10
11
function enclaveStatus() {
cockpit
.spawn(["enclave", "status", "--json"])
.then(data => {
var statusDetails = JSON.parse(data);
// perform some actions here
})
.catch((err) => {
// handle error
});
}
As you can see, the spawn() method accepts your command as an array of strings. From here it will return any output as a string. The command enclave status --json writes JSON to stdout so that gives us easy access to the data, which is easily parsed into JS Object and can then be manipulated as you’d expect.
Cockpit’s limitations
The Cockpit JS plug-in is incredibly powerful, but given it’s still being actively developed there are some issues. One of those is the documentation surrounding plug-in creation. And yes before you say it, I know that’s often a complaint of any development resource. But really right now there’s very little information about invoking privileged commands using sudo. For instance, when a system enrols to Enclave using the enclave enrol command, it requests elevated permissions to be able to put private keys in a safe place. You can force elevated permissions with a flag which does work but again can cause its own issues - your mileage my vary.
Another issue right now is you can watch a file for changes, but not a directory. While a directory watch could be achieved with an ls followed by a series of individual watchers, during testing I wasn’t quite getting the results I expected.
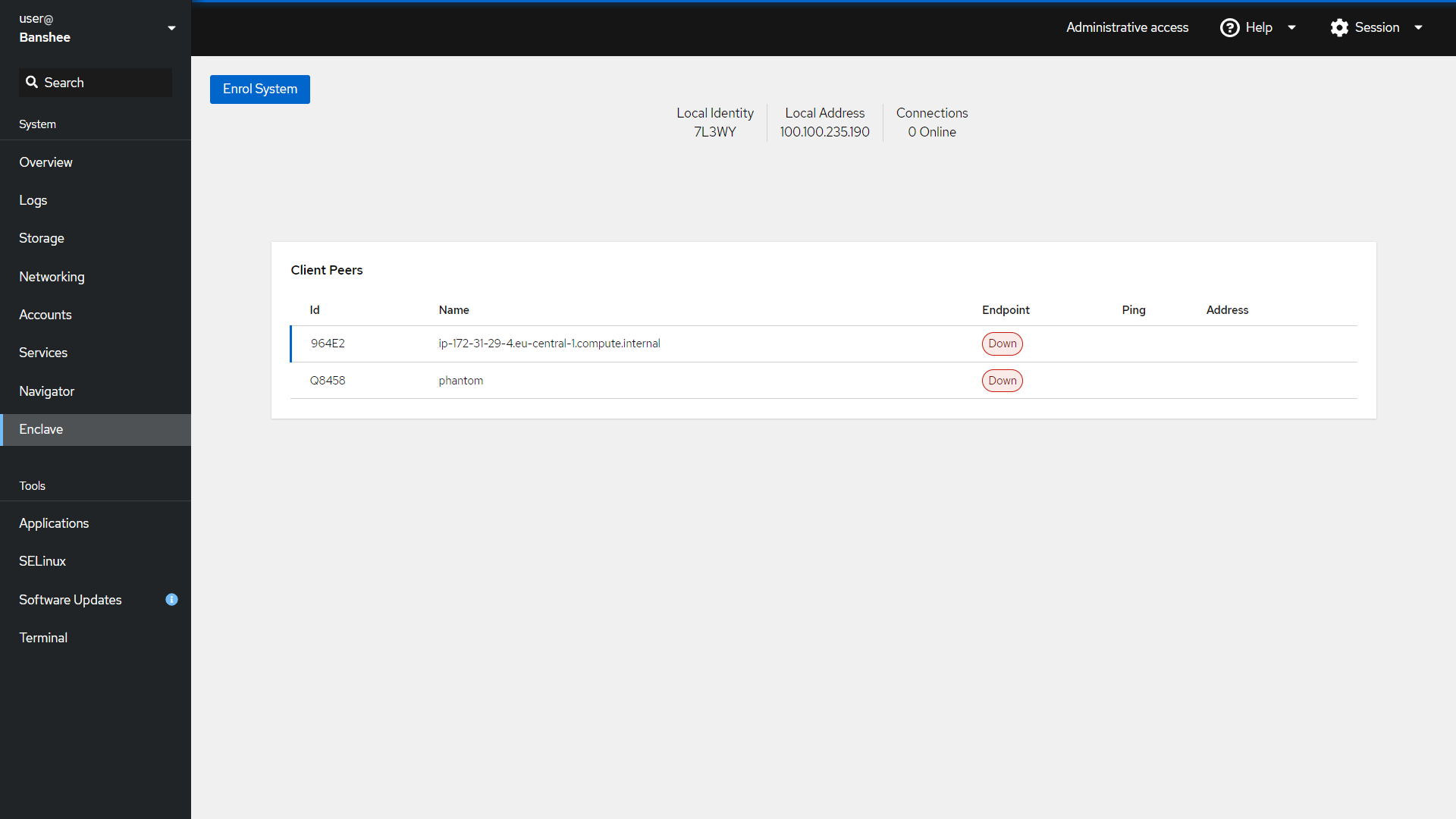
What can you do with the Enclave plugin?
With the first release of our plug-in for Cockpit, you will be able to see the status of Enclave and your connections to other peers. You will also be able to start and stop the Enclave daemon and the plugin will help you with the initial enrolment of your system.
Future plans
We’ve made the plug-in open source; you can find it on GitHub here: https://github.com/enclave-networks/cockpit-enclave. RPM and Deb packages are available too, which in time will also be made available through apt and yum repositories.
I hope you find this project useful and would encourage you to fork and raise a PR if you have any changes you’d like to make. Or alternatively if there’s something wrong or you’d like to request an enhancement submit it here! Myself and the rest of the Enclave team would love to see what you come up with!