The DevOps approach and philosophy has radically changed how organisations deliver agile solutions that provide value to customers and competitive advantage.
So much of the DevOps toolkit, culture and philosophy is about collaboration between teams and functions and effective, lean business processes.
At Enclave Networks we have long realised that infrastructure management needs to play its part in adopting a DevOps approach. At the moment, unfortunately the network is often a blocker to getting things done. It’s a complex array of functions, responsibilities, tools, hardware, apps and processes that have been built layer upon layer, often over decades. When Enclave Networks assists our customers, we very often see how the network is a blocker to business imperatives and source of cost, delay and inertia.
For example, under Open Banking legislation, financial institutions must expose data to third parties. This can be problematic. We have seen organisations battle with the complexity of creating secure connections between their network and that of a third party. The result is network infrastructure projects that take weeks, perhaps even months, to deliver. The costs are clear, both in valuable resources and time but perhaps less obviously in potential security vulnerabilities. Complexity is the enemy of security.
Enclave Networks can help solve these problems by simplifying, consolidating and automating network infrastructure management. The net result is that connections, that used to take weeks and months to deploy, can be live in minutes and without making any changes to the underlying network infrastructure. Firewalls stay closed and there is no need to look at ACLs, NAT, routing tables, switches, routers, IP addresses and secret keys.
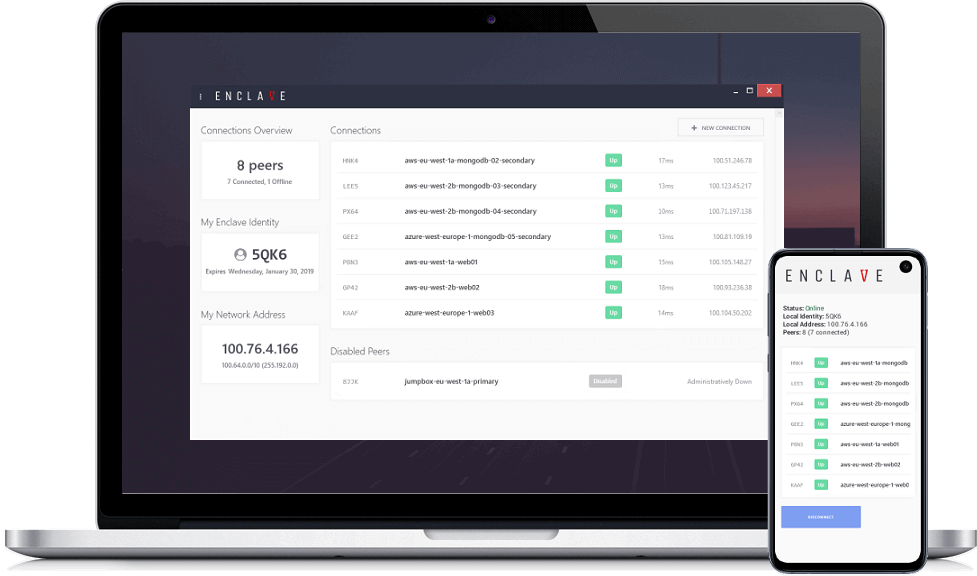
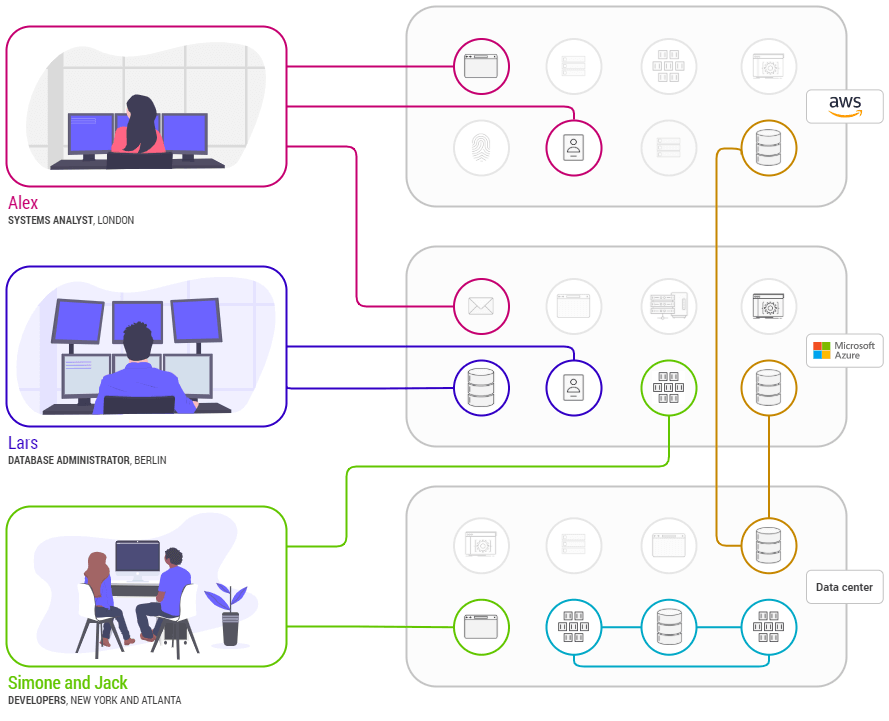
Enclave allows organisations to create peer to peer (not client/server), end to end encrypted connections at layer 2. Our patented “authenticate then connect” technology means that connections are invisible to the public internet and its possible to set and automate “guardrails” around your connections so that they work within specific constraints aligned to your policies. Because we are joining system to system, not network to network, we can more easily microsegment infrastructure for the intended purpose only; or in other words facilitate intent based networking.
Enclave can help deliver DevOps for your network.