
At Enclave Networks our mission is to help organisations simplify their network infrastructure management, whilst also making it more secure.
The challenge at the moment is, as we move to the Cloud and seek to integrate that with our on premise infrastructure, we introduce yet more layers of complexity to manage. We end up with myriad tools and processes to create and manage network connectivity.
As a result, we need teams of Systems Architects and Network Engineers just to manage that complexity and risk in order to get things done. We all too often inhabit a world where the network is a complex and costly blocker to productivity and innovation.
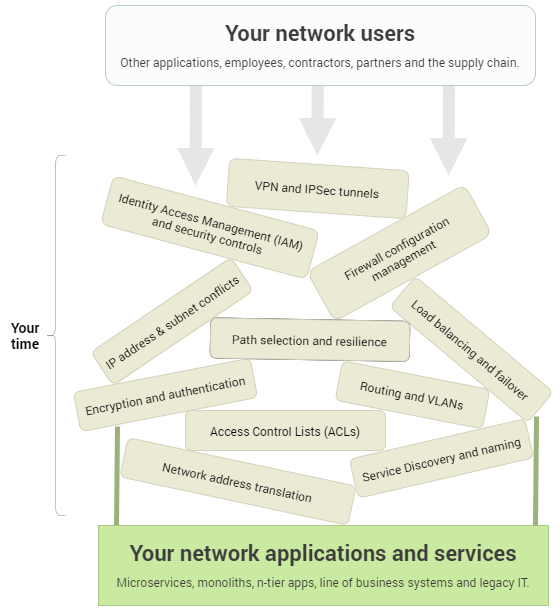
We all know that agility is imperative and we want to work in a DevOps environment and culture; but then the network gets in the way. This is because of the considerable time and costs of configuring and managing firewalls, VPNs, IP addresses, subnets, ACLs, NAT, routing tables, certificates and secret keys. Moreover, we also have to think about containers and micro-segmentation, how we work with stakeholders, third party collaborators and manage remote workers.
So much of what we do currently requires us to try to find secure ways to punch holes in our network perimeter to allow the necessary connectivity or to establish single points of concentration such as VPN servers, visible on the public internet, to route traffic.
Enclave allows for peer to peer (not client/server) connections. We utilise outward bound only traffic to create connections, so we can let the firewalls do their job, always closed, without exceptions. Because with Enclave, authentication happens before connection, all endpoints in an Enclave network are invisible to the public internet. It’s much harder to target and attack something you don’t even know is there.
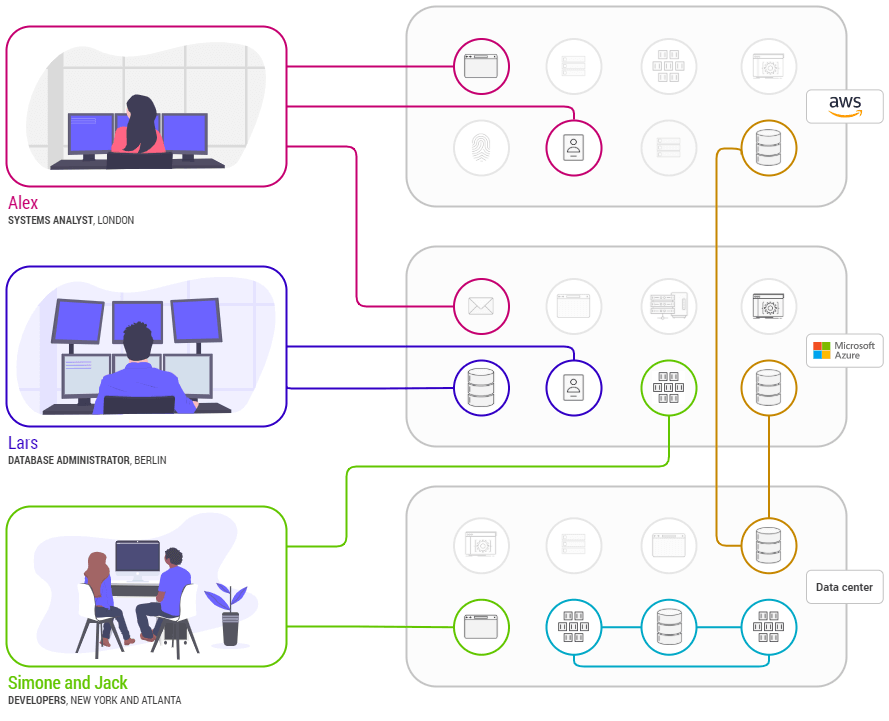
This means we move to an approach where we are not trying to connect networks together or punching holes in perimeters but simply creating the system to system connectivity we need. So, for example, we have a business imperative to move data from system 1 in my network to system 2 in your network and it just happens; in minutes, not weeks or months; all without touching a firewall or an ACL.
Enclave creates peer to peer, end to end encrypted, mutually authenticated connections at Layer 2 and because it’s Layer 2, a whole range of traffic can utilise the connection.