A VPN portal providing access to company secrets. Graphic by Vecteezy
With the acceleration to a mobile-first workforce and cloud transformation, the traditional network can no longer be trusted. We require new ideas and technologies to support new ways of working.
The problem is that for the last twenty years, traditional VPN technology solutions have been broken tools, based on a flawed concept: connect first, then authenticate.
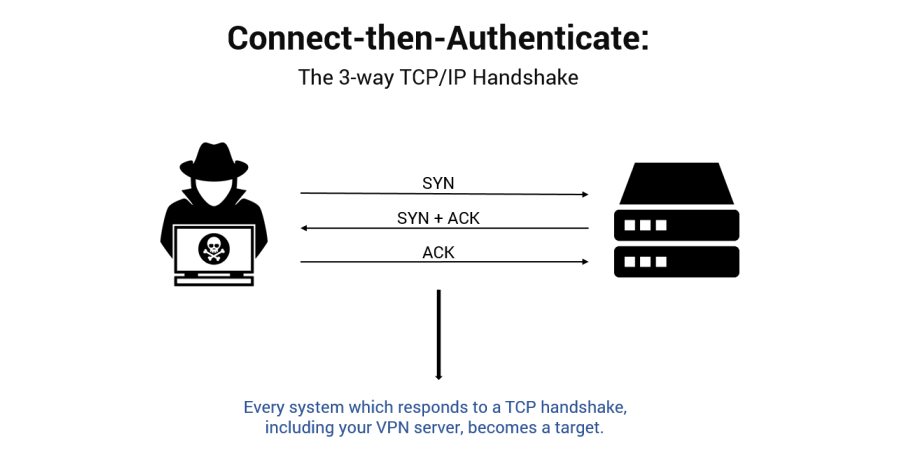
Your VPN server (and any other Internet facing infrastructure) is by definition, exposed. Dutifully running 24 hours a day, waiting to receive connections from mobile workers, partners and your supply chain. Discoverable and reachable from anywhere on the public Internet.
Your humble VPN server is a primary point of attack and leverage against your organisation.
Your VPN server is susceptible to unpatched vulnerabilities, previously unknown or newly discovered zero-day exploits, denial of service attacks, and spear phishing campaigns targeting credential theft — all because it responds to the 3-way TCP/IP handshake.
We’ve taken a different approach.
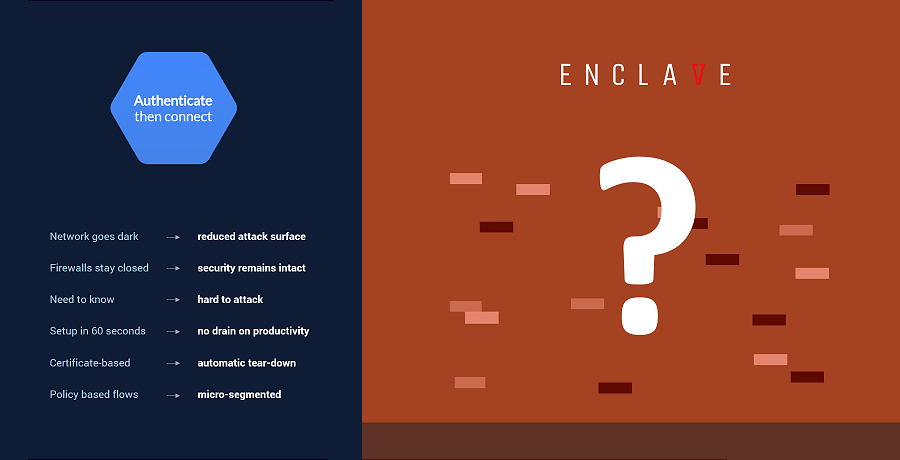
Enclave reverses this paradigm by placing authentication first, before a connection can take place.
Aligned to the philosophy of zero trust network access, authenticate-then-connect renders your network dark; invisible to would be attackers.
Without listening ports, visible IP addresses or DNS records, your infrastructure goes dark to attackers.
Enclave wraps a Zero-Trust, Software-Defined Perimeter around existing applications and systems, building direct peer-to-peer connectivity without opening ports — allowing organisations to keep their firewalls completely closed.
Without listening ports, visible IP addresses or published DNS records, connectivity is established on a need-to-know basis and your infrastructure goes dark; resistant to discovery, targeting and attack.
Enclave is also a zero-configuration platform. It just works.
There is no need to frustrate over access control lists, adjust DNS entries, configure routing tables, plan your subnets, avoid IP address conflicts or deploy additional servers to the network perimeter.
More over, Enclave is deployable incrementally, without requiring changes to existing network infrastructure.
Put simply, we’re not here to build a better network, we’re here to get the network out of the way.
Unleash your network, remove complexity, adapt quickly to changing business requirements, lower your costs, darken your infrastructure and please, close your firewall.