
Enclave Networks’ customer, Northern Star, recently shared an interesting use case with us, which is a great illustration for all systems architects and network engineers on how to use Enclave to create network connections easily and securely.
Northern Star are a significant global Managed Services Provider (MSP), managing IT infrastructure for a wide range of enterprises. Many of their clients require data to be moved between different cloud services and between on premise systems to the Cloud. This is typically a machine to machine environment and often includes headless servers. For network engineers this can be a real drag because it’s a time consuming process, which requires planning and careful execution so as not to introduce security vulnerabilities because of the multiple tools and systems that require changes in order to facilitate the connections.
Roy Barnes, UK Director of Northern Star, said “Enclave has helped us simplify everyday tasks and reduce the burden on our infrastructure engineers. Enclave is a driver of productivity, whilst also improving inherent security.”
Northern Star is using Enclave to quickly and safely migrate on-premise databases to newly created Cloud-hosted replacements. Once migrated, employees continued to access the new Cloud environments safely and securely using Enclave, without the hassle of configuring firewalls, Access Control Lists (ACLs), routers, secret keys, Network Address Translation (NAT), encryption and traditional remote access solutions.
Moreover, complexity is the enemy of security. Enclave simplifies and automates these processes by allowing peer to peer, client to client, end to end encrypted connections to be set up instantly and removed just as quickly if required. Enclave consolidates tasks, functions and systems planning, reducing the complexity of setting up new connections and transferring data. Because Enclave allows “guard rails” to be put around systems it means constraints can be applied which automatically control the way in which connections are made, managed and used. So for example, it is possible to ensure that connections can only be used to send and/or receive certain types of traffic or to ensure they automatically expire after a defined period of time or event as defined in organisation protocols and procedures.
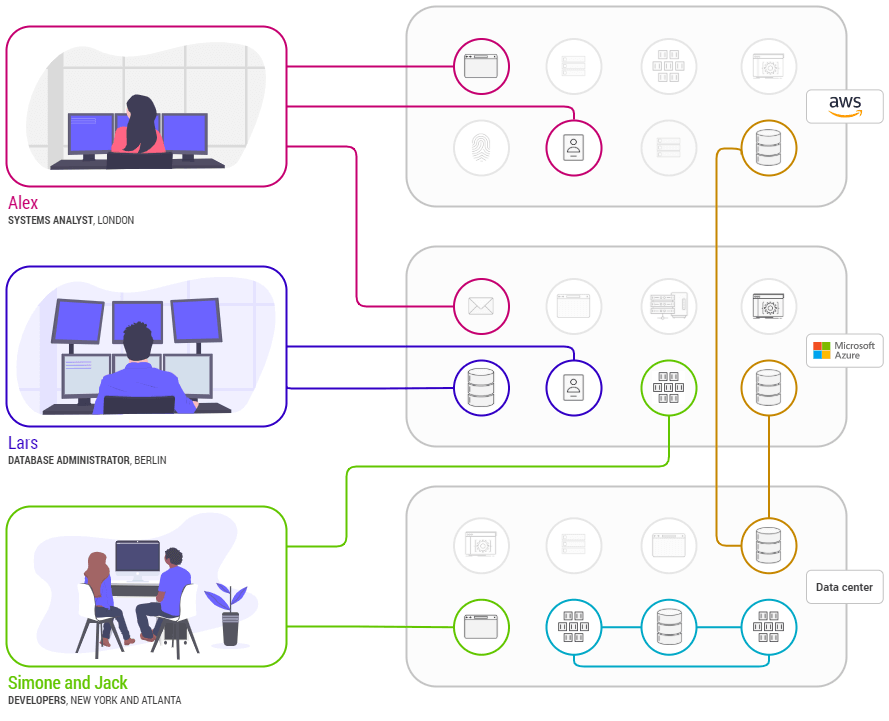
This means that the burden and costs of setting up and then closing down network connections is greatly reduced and, because certain processes are automated and far less complex, there is a significant reduction in the security risk vector.