
The phrase Zero Trust is not new, but it’s increasingly gaining traction in network infrastructure circles.
Conceptually, Zero Trust is relatively straightforward in that, instead of building castle walls around your network and defending that perimeter against outsiders, you assume that no system or endpoint, either inside or outside your castle walls, should be trusted by default. At Enclave, we think of this as Endpoint Defined Perimeters (EDP).
As organisations embrace the opportunities of cloud infrastructure, integrate cloud with on prem; as team members are increasingly operating outside our premises and as applications become more complex and diverse, we need a different approach to assigning and managing trust and affording access to our critical network infrastructure.
Zero Trust Network Access (ZTNA) takes nothing for granted; identities must always meet trust standards, access must be provided only on a need to know basis, systems need to be micro-segmented and continuously checked, verification and trust must be established, not assumed.
So, for example, a Zero Trust approach aims to mitigate many of the risks associated with traditional VPN connectivity. That risk being that if someone maliciously manages to authenticate themselves through your remote access VPN server, then they are inside your castle walls and can often move around freely (lateral movement).
Indeed, that risk only exists because most remote access VPNs work on the basis that they’re freely accessible to anyone on the public internet. In other words they operate on a “Connect first, then Authenticate” basis.
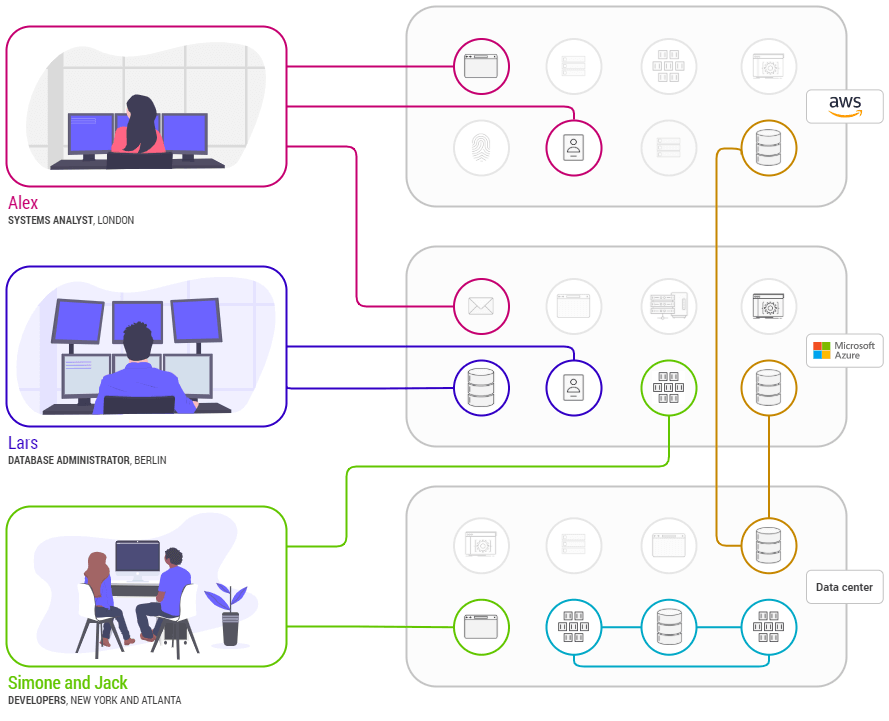
At Enclave Networks, Zero Trust is at the heart of everything we do, from our patented technology and our authenticate first, then connect approach to network connections, through to how we allow centralised, policy based management of network infrastructure.
So instead of punching holes in network perimeters to allow access, we ensure firewalls always stay closed (and doing their job) and that systems are connected together in a micro segmented, end to end encrypted, peer to peer way.